Thbusiness V2 0 3 Exploit Walkthrough The aim of this walkthrough is to provide help with the Unified machine on the Hack The Box website Please note that no flags are directly provided here Moreover be aware that this is only one of the many ways to solve the challenges It belongs to a series of tutorials that aim to help out complete beginners with finishing the Starting Point TIER 2 challenges
How about we begin by running a Rustscan to check which ports are currently being used rustscan a bash IP unlimit 5000 We ve identified two ports one for HTTP and the other for HTTPS services If we visit our machine s IP address we ll notice a redirect to https bizness htb Let s add that to our etc hosts file 1 Use the exploit to upload a malicious file to the vulnerable application containing whatever command we wish to execute where the web server will run this malicious file to execute the code 2
Thbusiness V2 0 3 Exploit Walkthrough

Thbusiness V2 0 3 Exploit Walkthrough
https://raxis.com/blog/wp-content/uploads/2022/11/CD8AB7BB-5728-4A7B-BEAF-9B24E818981A.jpeg

THBusiness WordPress Theme WordPress
https://i0.wp.com/themes.svn.wordpress.org/thbusiness/2.0.7/screenshot.png?w=1144&strip=all

Exploit Et Performance YouTube
https://i.ytimg.com/vi/-Nd1MZWoJnk/maxresdefault.jpg
2 Hi It is time to look at TryHackMe s Upload Vulnerabilities room Upload vulnerabilities are an extremely useful and exciting field so let s go I am making these walkthroughs to keep Introduction to WordPress Security WordPress is the application behind more than 30 of all websites Its ease of use and open source base are what make it such a popular solution The number of installs continues to grow there are now an estimated 75 million WordPress sites This popularity makes it a target for bad guys aiming to use a compromised web server for malicious purposes
1 An attacker makes a request to a website vulnerable to SQL Injection with an injection payload 2 The Website makes an SQL query to the database which also passes the hacker s payload 3 1 UNIT 2 Exploits on Metasploitable 3 Windows Abstract This unit focuses on penetration testing and the main objective is to perform penetration testing on Metasploitable 3 to exploit vulnerabilities and to escalate privileges to administrator rights or higher
More picture related to Thbusiness V2 0 3 Exploit Walkthrough

THBusiness Pro WordPress Theme
https://themezhut.com/wp-content/uploads/2014/10/THBusiness-Pro-Desktop.jpg

After The Ankr Exploit Helio Protocol Was Hacked Over 15M
https://coinbold.io/wp-content/uploads/2022/12/After-the-Ankr-Exploit-Helio-Protocol-was-hacked-over-15M.-jpg.webp
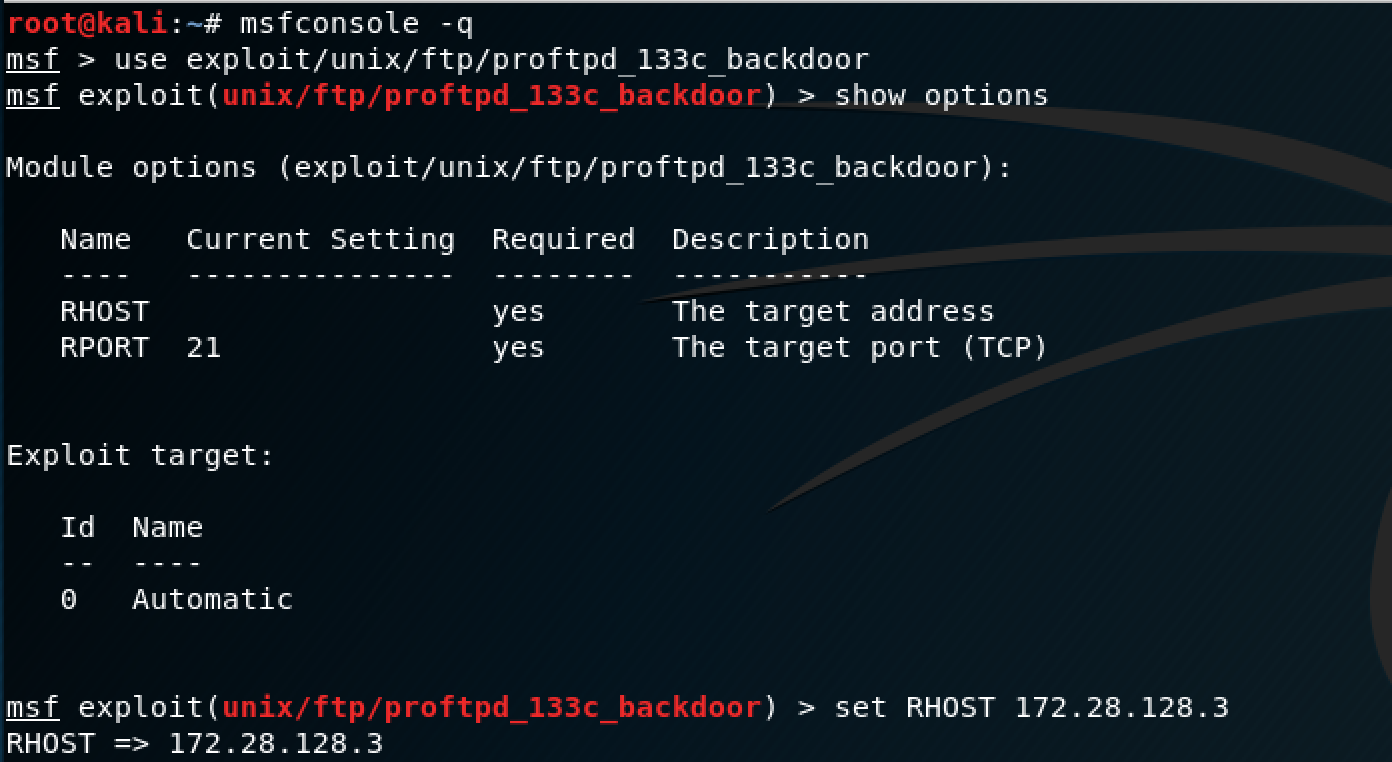
Basic Pentesting 1 Walkthrough
https://akvilekiskis.com/work/pentesting/bpt1ss/ftpexploit.png
The Rapid7 Metasploit community has developed a machine with a range of vulnerabilities Metasploitable 2 VM is an ideal virtual machine for computer security training but it is not recommended as a base system Saved searches Use saved searches to filter your results more quickly
2 Getting initial access and exploitation using searchsploit in kali Linux search for an exploit for samba 3 x 4 x here we get the Metasploit exploit for Samba 3 0 20 3 0 25rc3 Username map script Command Execution Metasploit but our goal is to exploit without Metasploit for first let us try to search for CVE for this Let s download the RCE exploit into our attacker s machine Firstly we should test if the Python script works on our attacker s machine The malicious code will look as shown in the screenshot above However we need to start our listener on our attacker s machine Let s execute the Python Script with the command I show above
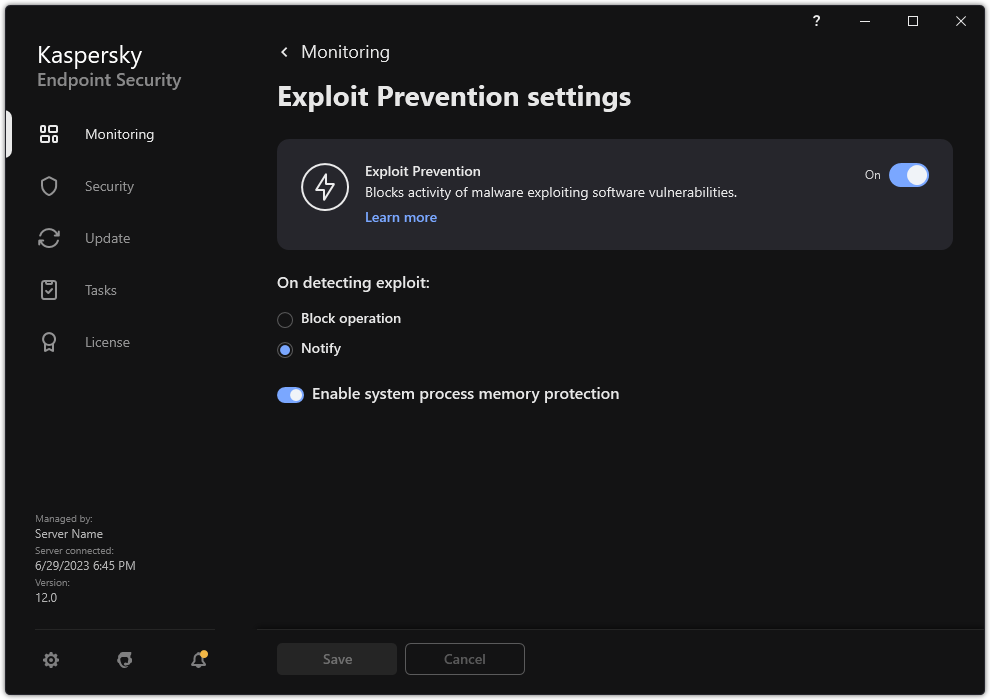
Enabling And Disabling Exploit Prevention
https://img.kaspersky.com/oh/KESWin/12.2/en-US/loc_screen_kes11_exploitpreventionsettings.png

Silent DOC Exploit 2023 FUD DOC Exploit 2023 Buy DOC Exploit Builder PoisonTools
https://poison.tools/wp-content/uploads/2022/10/exploit-doc-product-box.png
Thbusiness V2 0 3 Exploit Walkthrough - 1 UNIT 2 Exploits on Metasploitable 3 Windows Abstract This unit focuses on penetration testing and the main objective is to perform penetration testing on Metasploitable 3 to exploit vulnerabilities and to escalate privileges to administrator rights or higher