Operating System Security Tryhackme Walkthrough Operating System Security TryHackMe Walkthrough Write Up Aksshita Gupta Follow 13 min read Mar 20 2022 Task 1 Introduction to Operating System Security Every day you use a
Answer abc123 Once you are logged in as Johnny use the command history to check the commands that Johnny has typed We expect Johnny to have mistakenly typed the root password instead of a 0 00 16 58 TryHackMe Operating System Security HackToLearn 964 subscribers Subscribe Subscribed 46 Share 5 4K views 1 year ago SOUTH AFRICA Learn how users are introduced to Operating
Operating System Security Tryhackme Walkthrough
Operating System Security Tryhackme Walkthrough
http://www.shieldedsystems.com/images/courses/operating-system-security.jpg
Operating System Security TryHackMe Walkthrough Write Up By Aksshita Gupta Medium
https://miro.medium.com/v2/resize:fit:1140/0*sQZb7aJQ9plNGFGT.png
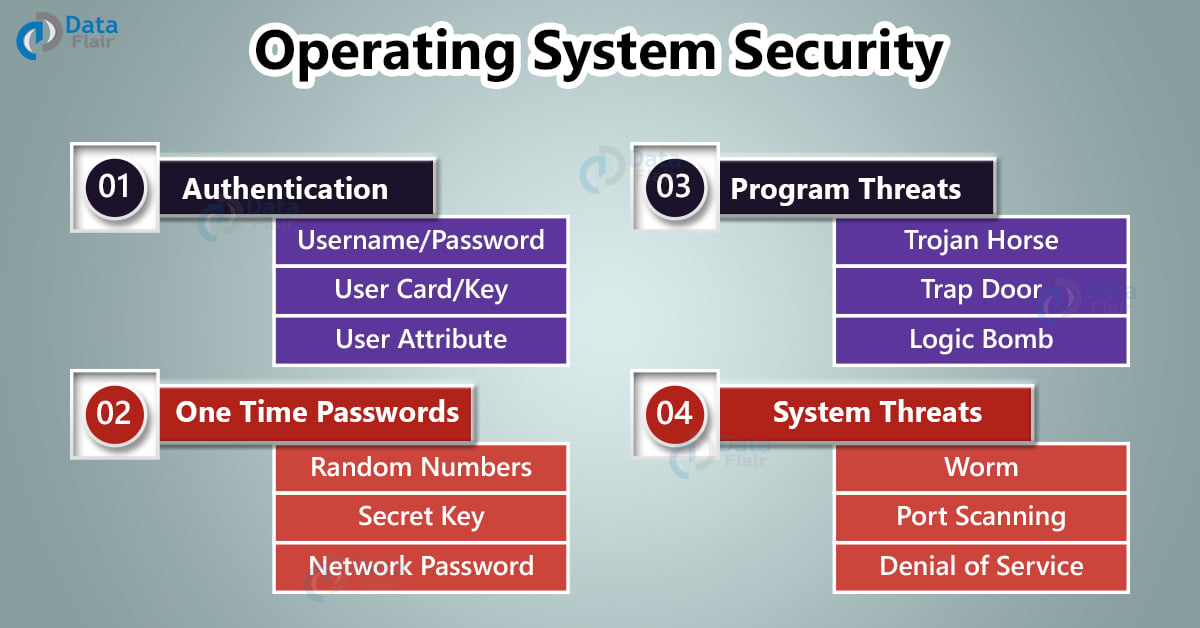
Operating System Security DataFlair
https://data-flair.training/blogs/wp-content/uploads/sites/2/2021/08/OS-SECURITY.jpg
This video gives a demonstration of the Operating System Security Room that is a part of the Introduction to Cyber Security pathway on Tryhackme Room Link h What is the password for the user johnny level 4 text Once you are logged in as Johnny use the command history to check the commands that Johnny has typed We expect Johnny to have mistakenly typed the root password instead of a command
Here is a walkthrough of the fifth room in the Introduction To Cyber Security path called Operating System Security Here is Operating System Security video walkthrough Enjoy comments sorted by Best Top New Controversial Q A Add a Comment Security Operations Monitoring Learn how to configure and utilise tooling to ensure that suspicious activity is quickly identified and dealt with in your environment Defenders use a variety of tools that make up the security stack such as Security Information and Event Management SIEM and Endpoint Detection and Response EDR tools
More picture related to Operating System Security Tryhackme Walkthrough

Operating System Cyber Attacks And Security TryHackMe Introduction To Cybersecurity
https://motasem-notes.net/wp-content/uploads/2023/08/maxresdefault-950x500.jpg

Operating System Security TryHackMe Walkthrough YouTube
https://i.ytimg.com/vi/-DNACLqGlH4/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH-CYACxgWKAgwIABABGFAgVyhlMA8=&rs=AOn4CLCWqPiN_LXmnG9hNFZ8kX_caTf2sw

Operating System Security TryHackMe Walkthrough YouTube
https://i.ytimg.com/vi/CRM9Bz5KfcM/maxresdefault.jpg
Introduction to Offensive Security Understand what Offensive Security entails and practice breaking into computer systems by exploiting applications and networks Start by learning the basics of web application security and practice exploiting a vulnerability in an online website Investigate operating system security and break into a target About This Walkthrough In this walkthrough I try to provide helpful information about the topics covered by the room I don t just give you the answers or copy what is already on TryHackMe Sometimes I will also review a topic that isn t covered in the TryHackMe room because I feel that it may be a useful supplement
This module will explore everything from getting started with using Windows to attacking common flaws that are found in common Windows systems Free Windows Fundamentals 1 In part 1 of the Windows Fundamentals module we ll start our journey learning about the Windows desktop the NTFS file system UAC the Control Panel and more Free Animesh Roy Classroom Posts Try Hack Me Operating System Security WriteUp Animesh Roy Monday May 16 2022 9 minutes read Update at Monday May 16 2022 OverView This room introduces users to operating system security and demonstrates SSH authentication on Linux Introduction to Operating System Security

TryHackme Operating System Security Walkthrough YouTube
https://i.ytimg.com/vi/2adwQOeBEU8/maxresdefault.jpg

5 Operating System Security TryHackMe Walkthrough YouTube
https://i.ytimg.com/vi/Irz-IbZvyOc/maxresdefault.jpg
Operating System Security Tryhackme Walkthrough - This walkthrough introduces users to operating system security and demonstrates SSH authentication on Linux Operating system security refers to the measures