Mongodb 2 2 3 Nativehelper Apply Remote Code Execution Walkthrough Blog http eromang zatazTwitter http twitter eromangMore on http eromang zataz 2013 04 03 cve 2013 1892 mongodb nativehelper apply remo
1 as part of a lab I am doing I need to exploit MongoDB I know I can input code into a search box that queries the MongoDB I have updated the code with my shell code but I won t include that I will just use the exploit as it is here This module exploits the nativeHelper feature from spiderMonkey which allows remote code execution by calling it with specially crafted arguments This module has been tested successfully on MongoDB 2 2 3 on Ubuntu 10 04 and Debian Squeeze Module Ranking and Traits Module Ranking
Mongodb 2 2 3 Nativehelper Apply Remote Code Execution Walkthrough

Mongodb 2 2 3 Nativehelper Apply Remote Code Execution Walkthrough
https://i.pinimg.com/originals/88/ff/66/88ff66dc204ff316da9af0a4cf9aafde.png
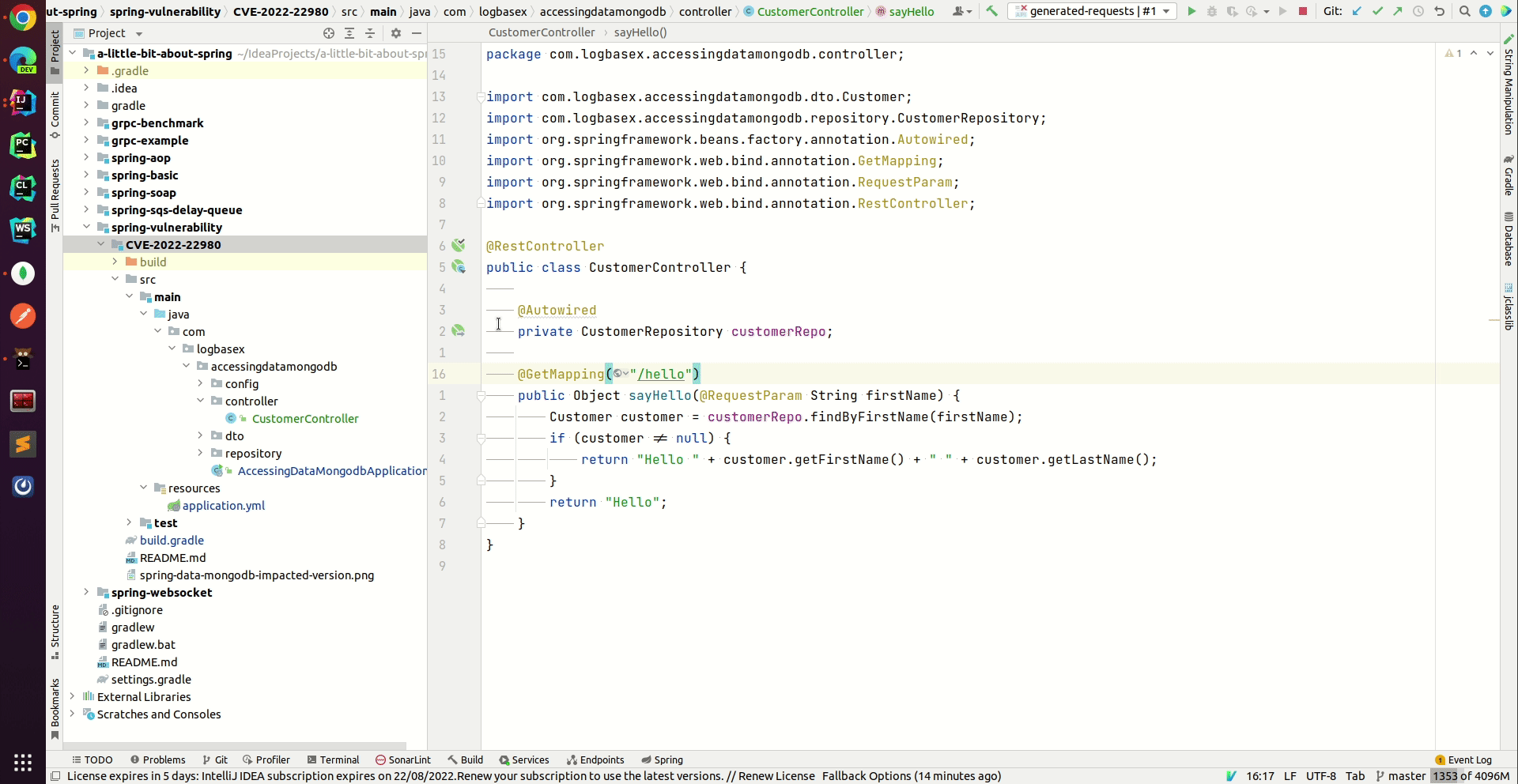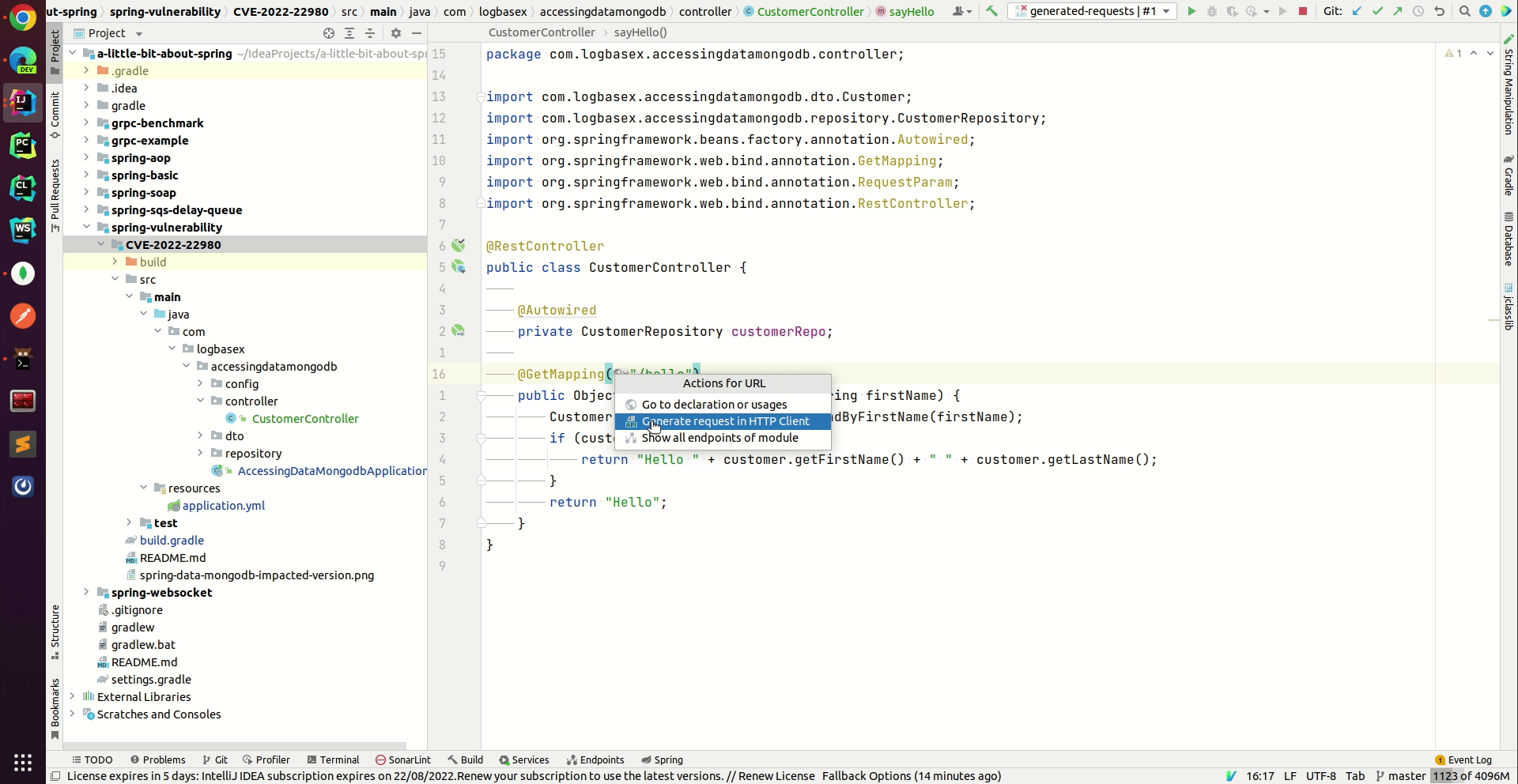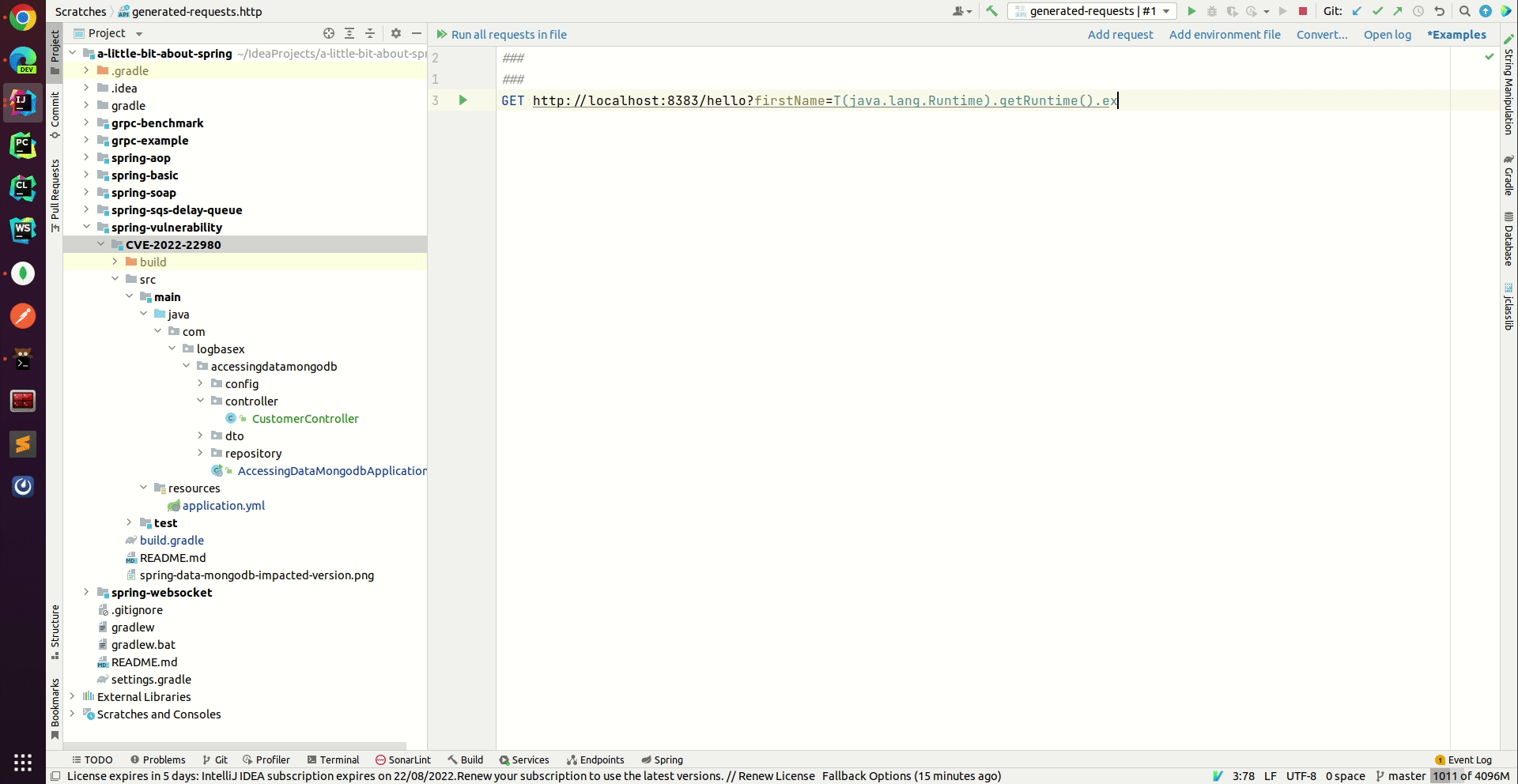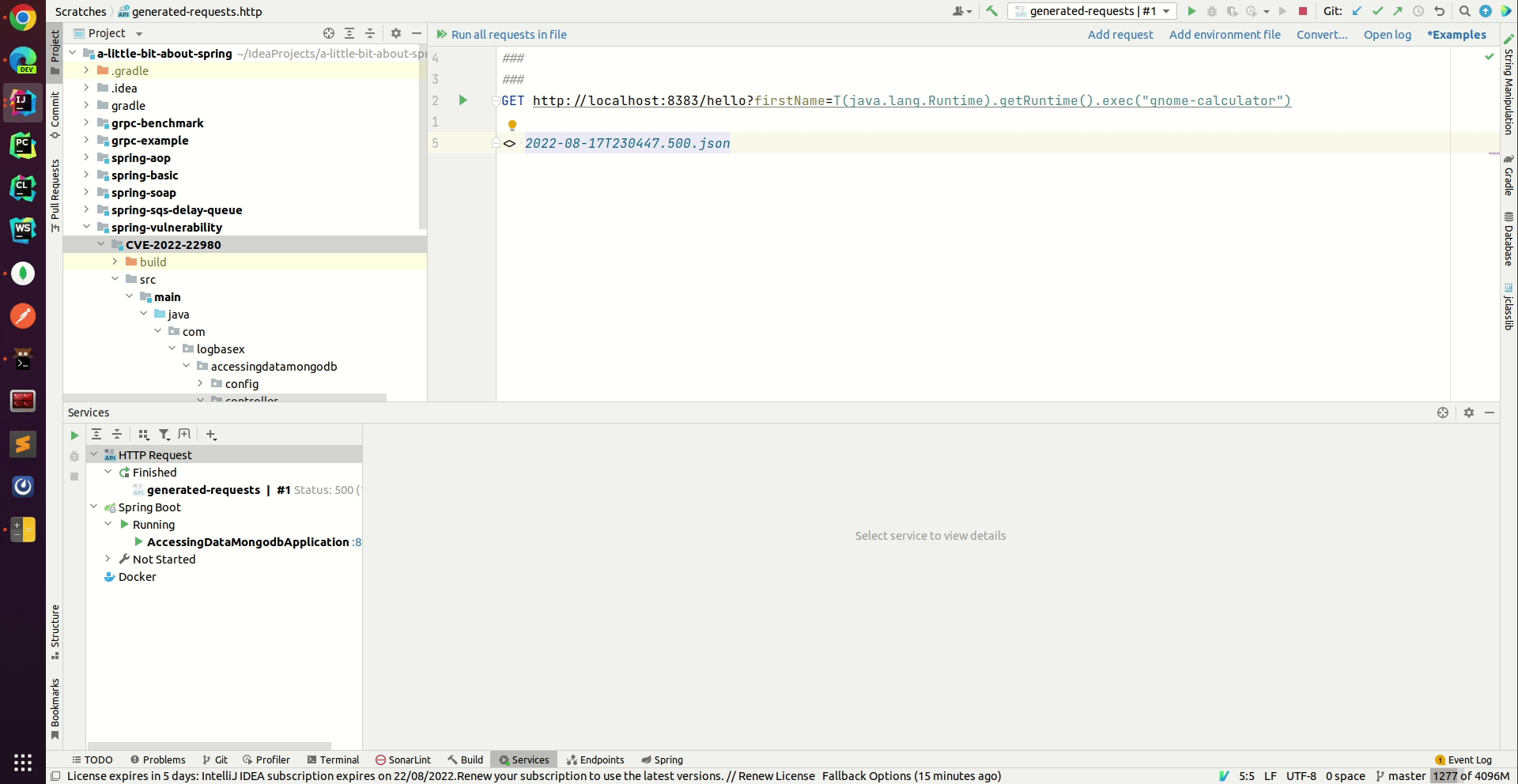
CVE 2022 22980 Spring Data MongoDB Remote Code Execution
https://images.viblo.asia/full/450a2c1e-803b-4531-addb-dc3423c61be2.gif

Remote Code Execution Using Mintegral s MTGInvocationBoxing YouTube
https://i.ytimg.com/vi/n-mEMkeoUqs/maxresdefault.jpg
MongoDB 2 2 3 nativeHelper apply Remote Code Execution EDB ID 24947 CVE 2013 1892 EDB Verified Author agix Type remote Exploit Platform Linux Date 2013 04 08 Vulnerable App If you have been following along closely you might have noticed versions 2 2 3 and below are vulnerable to more than just accessing them Specifically versions 2 2 3 and below makes use of the nativeHelper feature in the spidermonkey MongoDB implementation As it stands this only affects 32 bit Linux installs of MongoDB 2 2 3 and below
MongoDB nativeHelper apply Remote Code ExecutionThis module exploit a the nativeHelper feature from spiderMonkey which allows to to control execution by calling it wit specially crafted arguments This module has been tested successfully on MongoDB 2 2 3 on Ubuntu 10 04 and Debian Squeeze Thi Https vulners exploitdb EDB ID 24947 MongoDB 2 2 3 nativeHelper apply Remote Code Execution
More picture related to Mongodb 2 2 3 Nativehelper Apply Remote Code Execution Walkthrough

PDF Analysis Of Apache HTTP Server 2 4 49 Remote Code Execution RCE Attack Mitigation
https://i1.rgstatic.net/publication/370628616_Analysis_of_Apache_HTTP_Server_2449_-Remote_Code_Execution_RCE_Attack_Mitigation_Wijerathne_WND_-_IT20259884_Sri_Lanka_Institute_of_Information/links/645a64eb39c408339b37992f/largepreview.png

CORE JAVA Code Compilation Execution Java Code Execution Lecture 6 YouTube
https://i.ytimg.com/vi/8s1zbVaj35I/maxresdefault.jpg

How I Get Pre Auth Remote Code Execution CVE 2021 42237 On One Of The Vendors By Caesar
https://miro.medium.com/v2/resize:fit:1200/1*zTJzNYwYlWaLFpvG_vmHsw.png
This Metasploit module exploits the nativeHelper feature from spiderMonkey which allows control over execution by calling it with specially crafted arguments This Metasploit module has been tested successfully on MongoDB 2 2 3 on Ubuntu 10 04 and Debian Squeeze MongoDB nativeHelper apply Remote Code Execution CVE 2013 1892 CPAI 2013 1686
SQLi is one of the most common types of injection and at over a decade old is still going strong Injection issues aren t limited to just database languages Beyond SQL and NoSQL injection can occur in XPath XML Parsers SMTP headers and a wide variety of other contexts And as far as severity goes code injection is a cousin to RCE The application is now ready to scan To set up and run the scan we will use Invicti Standard For detailed information about scanning see our support page on MongoDB injection checks MongoDB injection checks are available in Invicti Standard versions later than 6 8 0 38168 and in Invicti Enterprise on demand since October 2022

Yet Another Log4j Patch Hoovers Up New Remote Code Execution Bug TechRadar
https://cdn.mos.cms.futurecdn.net/oYokkwQasq8QqtjHcyvWDH.jpg

WinRaR Remote Code Execution ThreatLocker
https://assets-global.website-files.com/640f78d90b310438f1fab4be/64ff5a9c3b5f462509b021f2_ThreatLocker_WinRaR_BlogImage.webp
Mongodb 2 2 3 Nativehelper Apply Remote Code Execution Walkthrough - If you have been following along closely you might have noticed versions 2 2 3 and below are vulnerable to more than just accessing them Specifically versions 2 2 3 and below makes use of the nativeHelper feature in the spidermonkey MongoDB implementation As it stands this only affects 32 bit Linux installs of MongoDB 2 2 3 and below