Mongodb 2 2 3 Exploit Walkthrough MongoDB is an open source database management system DBMS that uses a document oriented database model which supports various forms of data From here Default port 27017 27018 PORT STATE SERVICE VERSION 27017 tcp open mongodb MongoDB 2 6 9 2 6 9
For peneration testing lab purposes use the following steps to start the MongoDB instance p n p dir auto Launch MongoDB with the following command p n div class snippet clipboard content notranslate position relative overflow auto data snippet clipboard copy content root mongod httpinterface reset smallfiles pre class This module exploits the nativeHelper feature from spiderMonkey which allows remote code execution by calling it with specially crafted arguments This module has been tested successfully on MongoDB 2 2 3 on Ubuntu 10 04 and Debian Squeeze Module Ranking and Traits Module Ranking
Mongodb 2 2 3 Exploit Walkthrough

Mongodb 2 2 3 Exploit Walkthrough
https://s1.studylibid.com/store/data/004362878_1-7060a4f48e5e937758ba95e7b8639401-768x994.png
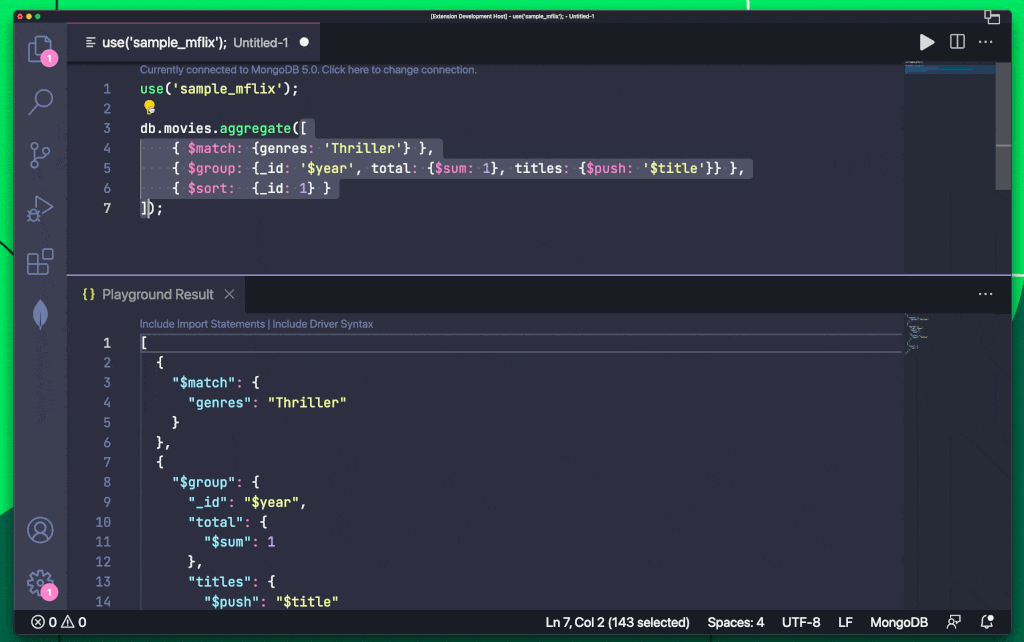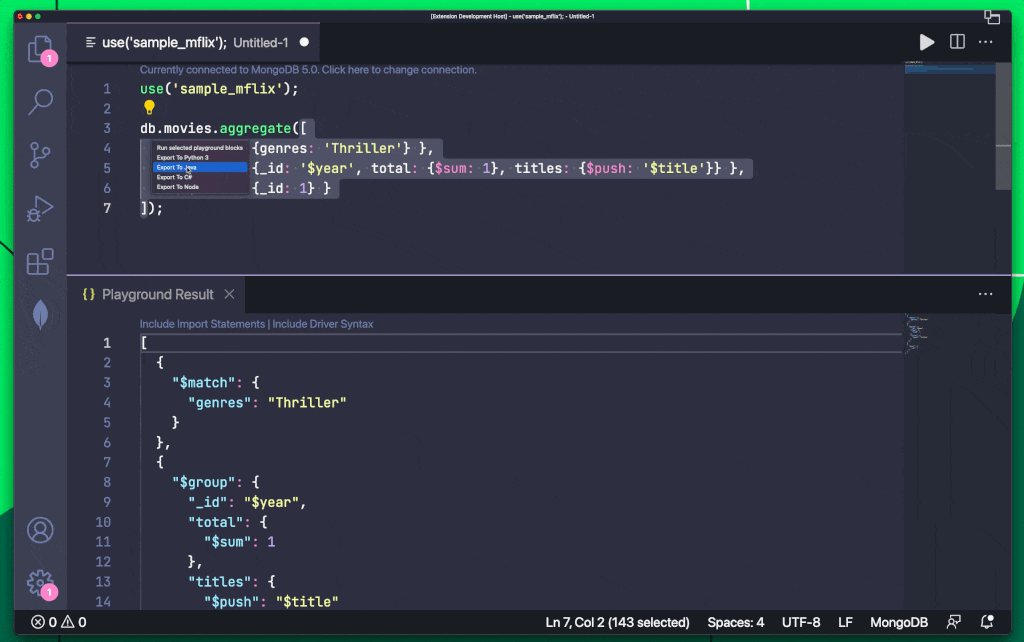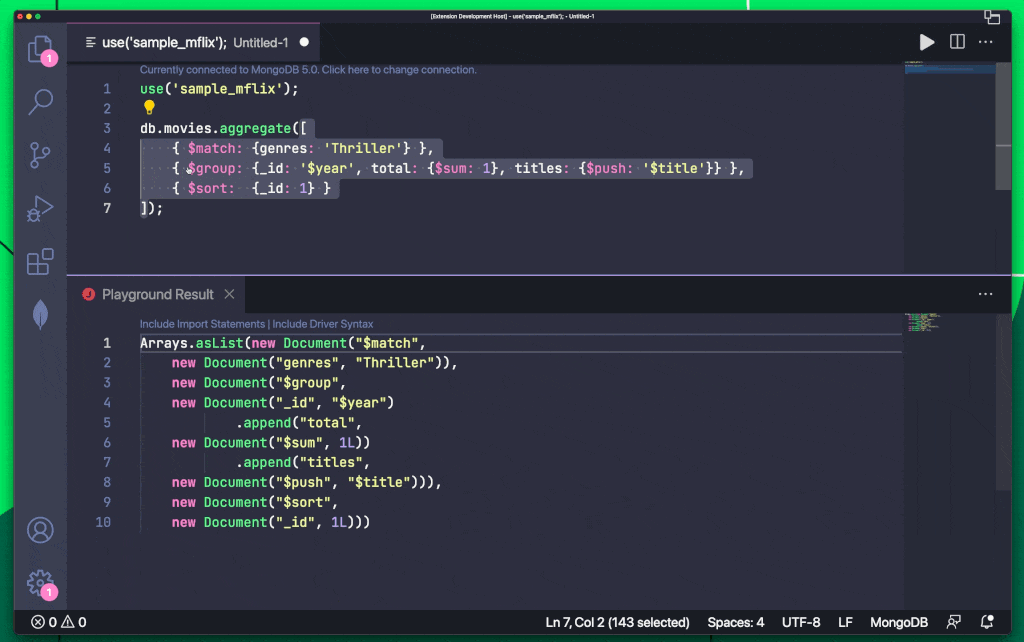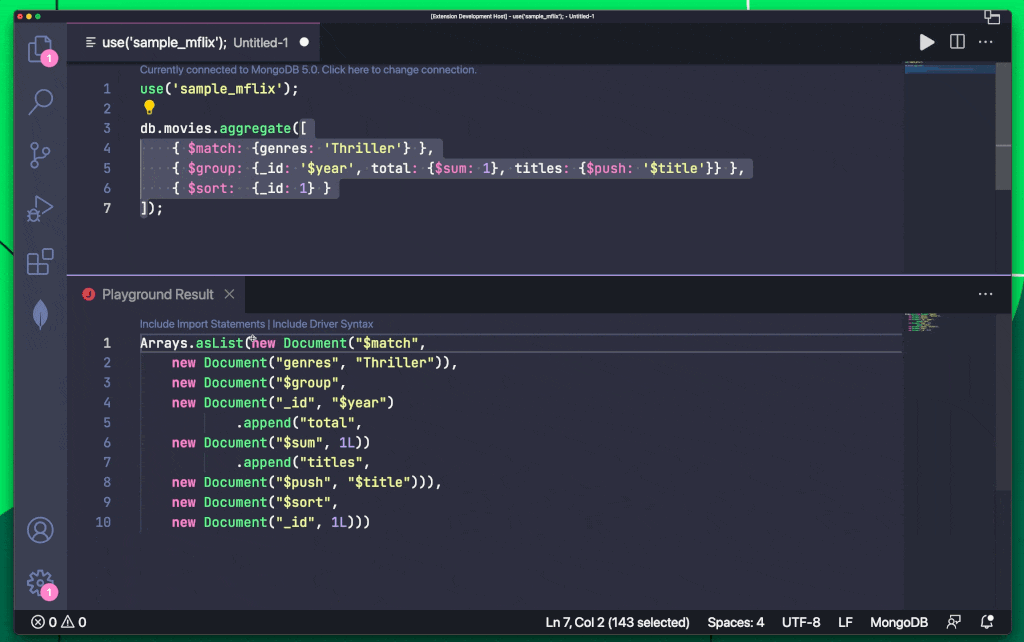
MongoDB On LinkedIn Check Out How You Can Export Queries To Your Favorite Programming 10 Comments
https://media-exp1.licdn.com/dms/image/C4D22AQEYDG5nOvmo3w/feedshare-shrink_2048_1536/0/1639788241353?e=2147483647&v=beta&t=2KUdBiLQCrJs9VbSHPhETs4LFO21CVfA0-AUutKFcYQ
GitHub Ajay Dhangar mongodb starter MongoDB
https://repository-images.githubusercontent.com/579927367/59c0d83f-88db-4b76-8449-65cab41b40be
MongoDB 2 2 3 nativeHelper apply Remote Code Execution CVE 2013 1892CVE 91632 remote exploit for Linux platform 1 Answer Sorted by 2 Looking at the error I m pretty sure you that this is related to one of the OSCP Lab machines You could get more help if you post these issues on the forum but here some tips shellcode is missing on you payload Check single and double quotes Share Improve this answer
This module exploits the nativeHelper feature from spiderMonkey which allows remote code execution by calling it with specially crafted arguments This module has been tested successfully on MongoDB 2 2 3 on Ubuntu 10 04 and Debian Squeeze Author s agix Platform Linux Exploiting MongoDB Injection Attackers can inject malicious code into queries if user inputs are not properly sanitized For example consider a login function that uses MongoDB javascriptCopy code 1 db users find username req body username password req body password 2 An attacker can exploit this by inputting
More picture related to Mongodb 2 2 3 Exploit Walkthrough

Introduction To MongoDB
https://cdn.hashnode.com/res/hashnode/image/upload/v1657557564953/z21J02QiM.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp

Connect MongoDB With PowerShell Delft Stack
https://www.delftstack.com/img/MongoDB/ag feature image - powershell mongodb.png
MongoDB Atlas
https://velog.velcdn.com/images/since-1994/post/8538abd6-1328-4258-acf6-eef88a3bd375/image.png
SQLi is one of the most common types of injection and at over a decade old is still going strong Injection issues aren t limited to just database languages Beyond SQL and NoSQL injection can occur in XPath XML Parsers SMTP headers and a wide variety of other contexts And as far as severity goes code injection is a cousin to RCE Mongodb features a REST API which can be activated by starting MongoDB with rest switch The port number of the HTTP interface is 1000 more than the configured MongoDB port so it is 28017 by default Developers are recommended to turn off the rest API and the HTTP interface on production servers since they allow direct access to the database
1 as part of a lab I am doing I need to exploit MongoDB I know I can input code into a search box that queries the MongoDB I have updated the code with my shell code but I won t include that I will just use the exploit as it is here MongoDB Cheat Sheet https webdevsimplified mongodb cheat sheet htmlMongoDB is a complex NoSQL database with a ton of commands and intricacies In this

MongoDB Pricing Actual Prices For All Plans Enterprise Too
https://revpilots.com/wp-content/uploads/2023/01/MongoDB-pricing.jpg
MongoDB Enhanced Data Management
https://media.licdn.com/dms/image/C5612AQGYK_Co9vxkAg/article-cover_image-shrink_600_2000/0/1620726657946?e=2147483647&v=beta&t=Rm8IGt9KhHhdqRVehCmnZUbtUXD3ATGLbzd-arWGKE0
Mongodb 2 2 3 Exploit Walkthrough - Exploiting MongoDB Injection Attackers can inject malicious code into queries if user inputs are not properly sanitized For example consider a login function that uses MongoDB javascriptCopy code 1 db users find username req body username password req body password 2 An attacker can exploit this by inputting