Minishare 1 4 1 Buffer Overflow Walkthrough In this blog post I will describe the exploitation process of a buffer overflow vulnerability in MiniShare 1 4 1 using the Immunity Debugger and the tools that come out of the box in Kali We can find MiniShare 1 4 1 here Vulnerability identification
MiniShare is a minimal web server with a simple GUI meant for fast and simple file sharing It was released back in a days of Windows XP Application has a buffer overflow vulnerability which is easy to detect and exploit That feature makes it a great candidate for OSCP BoF practice So here are some of the details about the buffer overflow Lab environment Victim Windows XP with Service Pack 3 192 168 8 105 Vuln App MiniShare 1 4 1 running on port 80 For Debugging Immunity Debugger Installed on Victim Attacking machine Kali Linux 192 168 8 102 4 15 kali2 amd64 1 SMP Debian 4 15 11 1kali1 x86 64 GNU Linux
Minishare 1 4 1 Buffer Overflow Walkthrough

Minishare 1 4 1 Buffer Overflow Walkthrough
https://varutra-1a3b6.kxcdn.com/wp-content/uploads/2017/05/Buffer-overflow-Copy.png

Guifre s Blog MiniShare 1 4 1 Remote Buffer Overflow Exploitation
https://3.bp.blogspot.com/-AkxeVEIB_zQ/WgbQsUVPSPI/AAAAAAAAY9k/C5Qp-x4j3E4DTXGIKXVz0ALyuRrL5y3JwCLcBGAs/w1200-h630-p-k-no-nu/Screen%2BShot%2B2017-11-11%2Bat%2B10.25.23.png
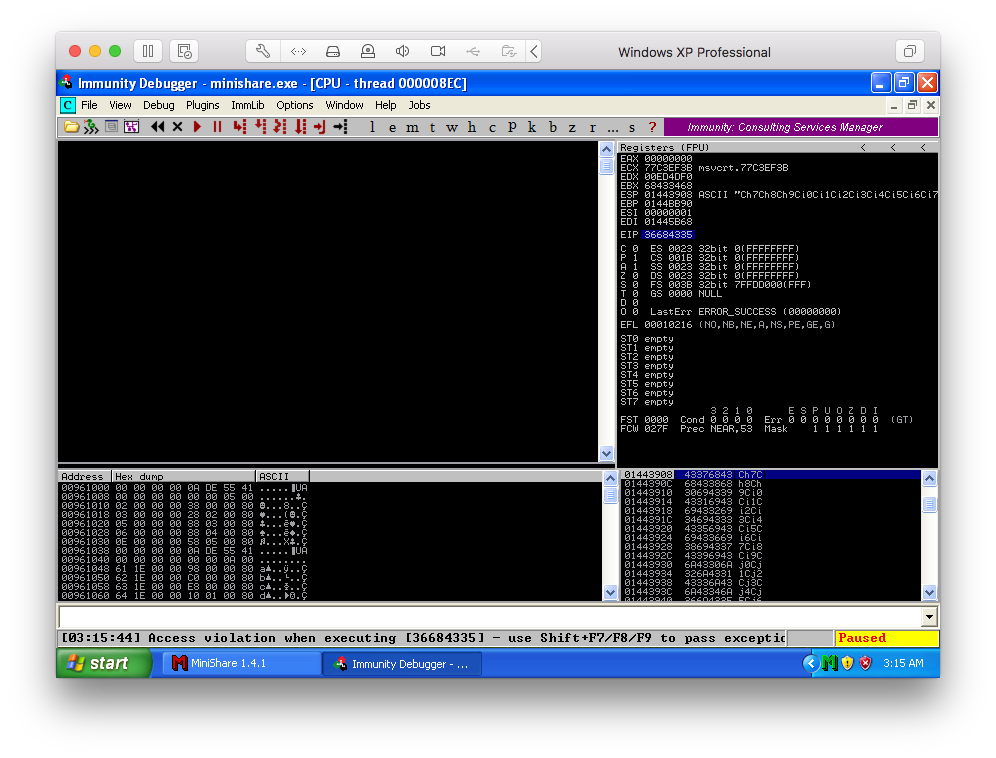
Guifre s Blog MiniShare 1 4 1 Remote Buffer Overflow Exploitation
https://3.bp.blogspot.com/-RofCh2TgseM/Wgbb_nIMGqI/AAAAAAAAY-A/ieH9lYhjtuI-BLkZtCflowWVLi73Ed1ywCLcBGAs/s1600/Screen%2BShot%2B2017-11-11%2Bat%2B11.15.57.png
This is a plain stack buffer overflow that requires a jmp esp to reach the payload making this difficult to target many platforms at once This module has been successfully tested against 1 4 1 Version 1 3 4 and below do not seem to be vulnerable Module Ranking and Traits Module Ranking Step 1 Discover the buffer size 1 We will use the code BoF MiniShare 1 py https github vry4n BoF MiniShare 1 4 1 blob main BoF MiniShare 1 py to discover the size of the buffer This is the line within the code will send the HTTP GET request s send b GET FUZZ encode b HTTP 1 1 r n r n
Hi all In this video I ve explained Buffer Overflow exploitation methodology with 2 popular vulnerable applications Minishare FreeFloat Hope this vide Description This is a simple buffer overflow for the minishare web server This flaw affects all versions prior to 1 4 2 This is a plain stack buffer overflow that requires a jmp esp to reach the payload making this difficult to target many platforms at once This module has been successfully tested against 1 4 1
More picture related to Minishare 1 4 1 Buffer Overflow Walkthrough

MiniShare Buffer Overflow YouTube
https://i.ytimg.com/vi/FWQtYlbQUU0/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AHuCYAC0AWKAgwIABABGDYgVSh_MA8=&rs=AOn4CLCPrSEGOM860eTa7fQskpnhLPxYYg

Buffer Overflow To RCE Brainpan Walkthrough EP4 YouTube
https://i.ytimg.com/vi/l2VJwJmOFZ8/maxresdefault.jpg

BANGLA TryHackMe The Cod Caper Buffer Overflow Walkthrough Penetration Testing CTF
https://i.ytimg.com/vi/K1TEZXKKyeY/maxresdefault.jpg
Buffer overflow in MiniShare 1 4 1 and earlier allows remote attackers to execute arbitrary code via a long HTTP HEAD request NOTE this product is discontinued References https nvd nist gov vuln detail CVE 2018 19861 https www exploit db exploits 45999 2004 11 07 Vulnerable App MiniShare 1 4 1 Remote Buffer Overflow Exploit v0 1 Bind a shellcode to the port 101 Full disclosure and exploit by class101 at DFind kd team n3ws at EFnet 07 november 2004 Thanx to HDMoore and Metasploit for their kickass ASM work
Saved searches Use saved searches to filter your results more quickly MiniShare Buffer Overflow Python exploit script for buffer overflow exploitation of MiniShare 1 4 1 The values that needs to be changed as per your requirements are commented out The shell used is bind shell once the script is executed for the target Attacker needs to connect through nc to the victim machine with port 1337

Labtainer Walkthrough Lab 1 Buffer Overflow YouTube
https://i.ytimg.com/vi/SP7c6uAaDh0/maxresdefault.jpg

PDF Buffer Overflow Part 1 DOKUMEN TIPS
https://img.dokumen.tips/doc/image/5695d5601a28ab9b02a51fe1/buffer-overflow-part-1.jpg
Minishare 1 4 1 Buffer Overflow Walkthrough - Step 1 Discover the buffer size 1 We will use the code BoF MiniShare 1 py https github vry4n BoF MiniShare 1 4 1 blob main BoF MiniShare 1 py to discover the size of the buffer This is the line within the code will send the HTTP GET request s send b GET FUZZ encode b HTTP 1 1 r n r n