Htb Academy Web Requests Walkthrough In this video I provide a walkthrough through the question in the GET section in the Web Requests module in HTB Academy
51 4 4K views 1 year ago This is a walkthrough in the first section of the HTB Academy module Web Requests more more Fast forward to better TV Skip the cable setup start The HTB Web Requests CTF challenge consists of several tasks that involve interacting with a web server using cURL and browser devtools Let s dive into each task and explore how to solve them Task 1 Downloading a File The first task requires us to download a file returned by the download php endpoint on the server
Htb Academy Web Requests Walkthrough

Htb Academy Web Requests Walkthrough
https://academy.hackthebox.com/images/pages/front/OG_AcademyHomepage.png

HTB Academy Offensive Attacking Web Applications With Ffuf 05311840000016 YouTube
https://i.ytimg.com/vi/ETdejHcom9E/maxresdefault.jpg
HTB Academy Attacking Web Applications With Ffuf By R4fik1 Medium
https://miro.medium.com/v2/resize:fit:1358/0*eYTuRkkUxCV3GOet.jpeg
HTTP Flow cURL Web requests sent through a browser Chrome Firefox and the cURL command line tool cURL client URL is a command line tool that mainly supports HTTP Ideal for scripts and Module Overview Fundamental General Summary This module introduces key fundamentals that must be mastered to be successful in information security Understanding web requests is essential for understanding how web applications work which is necessary before attempting to attack or secure any web application
Summary This module introduces core penetration testing concepts getting started with Hack The Box a step by step walkthrough of your first HTB box problem solving and how to be successful in general when beginning in the field In this module we will cover An overview of Information Security Penetration testing distros You need to send a get request to the ip and port provided from the provided machine and you need to set the parameters num1 and num2 with values so that num1 num2 1337 the url should look like this http 138 68 171 242 31729 flag php num1 1000 num2 337
More picture related to Htb Academy Web Requests Walkthrough

HTB Academy Web Requests HTTP Requests And Responses YouTube
https://i.ytimg.com/vi/E6H5FcL19Iw/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH-CYAC0AWKAgwIABABGDogVyhyMA8=&rs=AOn4CLBbkN7Is7MRf9I01PYznYLzXoJkNw

HTB Academy FFUF Directory Fuzzing Walkthrough YouTube
https://i.ytimg.com/vi/sHtZJci7TpA/maxresdefault.jpg

HTB Academy Web Requests YouTube
https://i.ytimg.com/vi/Ucxn1PIlG_s/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH-CYAC0AWKAgwIABABGDkgVihyMA8=&rs=AOn4CLCffooqtsoN0EPoWfp3Y5LHfV4k5w
Aug 28 2021 Before attempting HTB I advise completing the academy modules first as it really helps with the fundamentals in this blog I will be reviewing the first module Web WEB Requests POST Method HTB Content Academy Ic32K December 6 2021 7 25pm 1 Hello everyone I m a little bit stuck on this exercise and also a bit confused about the goal The last example shows that the web must be vulnerable to content type but I cannot make it happen
Academy Web Requests POST METHOD I m really struggling with this one On the POST Method module I ve got the question Login with the credentials guest guest and try to get to the admin user from what you learned in this section and the previous section In this video I provide a walkthrough through the exercises in the HTTP Requests and Responses section in the Web Requests module in HTB Academy

HTB Academy Web Requests HTTP Headers YouTube
https://i.ytimg.com/vi/9kWO2xepXhE/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH-CYAC0AWKAgwIABABGDYgWChyMA8=&rs=AOn4CLDx_VCAMADM23GfnD91QnGRdDFTlw
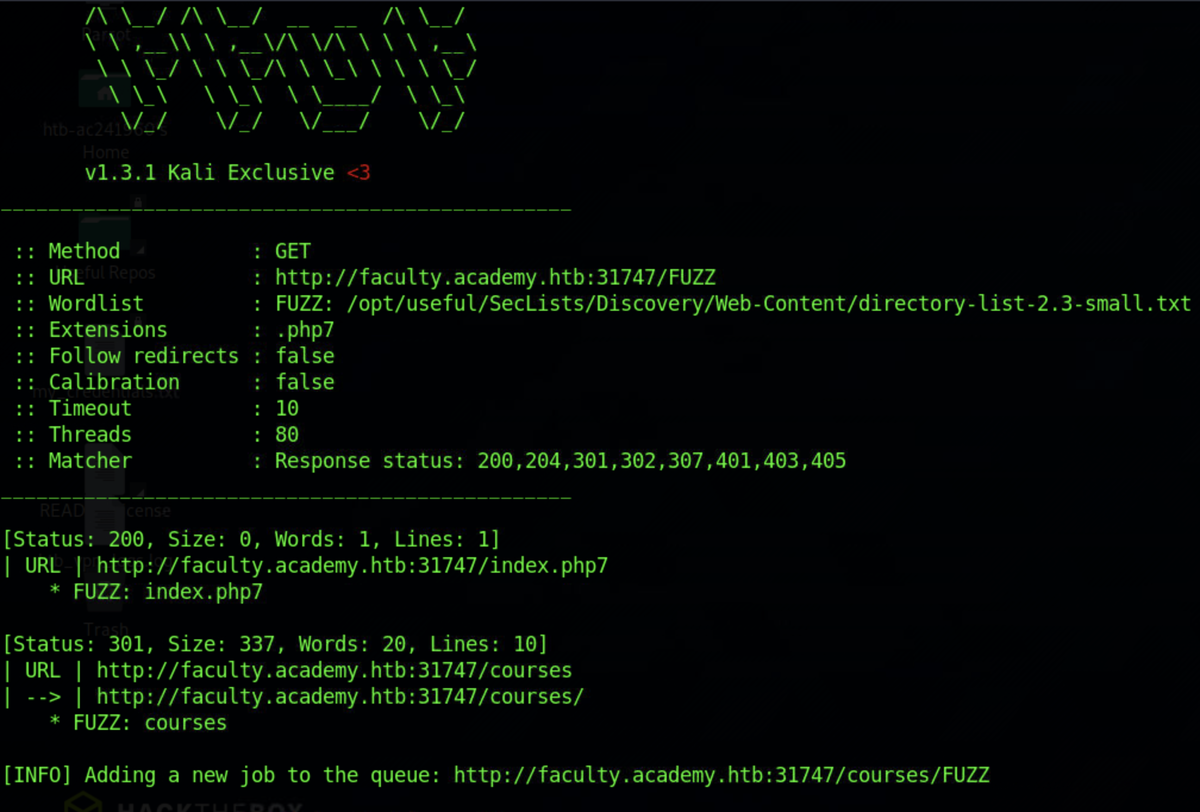
HTB Academy Attacking Web Applications With Ffuf Skills Assessment Walkthrough Charles Varga
https://charleskvarga.com/post/htb-academy-attacking-web-applications-with-ffuf-walkthrough/new_job_hu9733fd6154719904b6a53eaf2c3e747a_1388213_1200x1200_fit_lanczos_3.png
Htb Academy Web Requests Walkthrough - You need to send a get request to the ip and port provided from the provided machine and you need to set the parameters num1 and num2 with values so that num1 num2 1337 the url should look like this http 138 68 171 242 31729 flag php num1 1000 num2 337