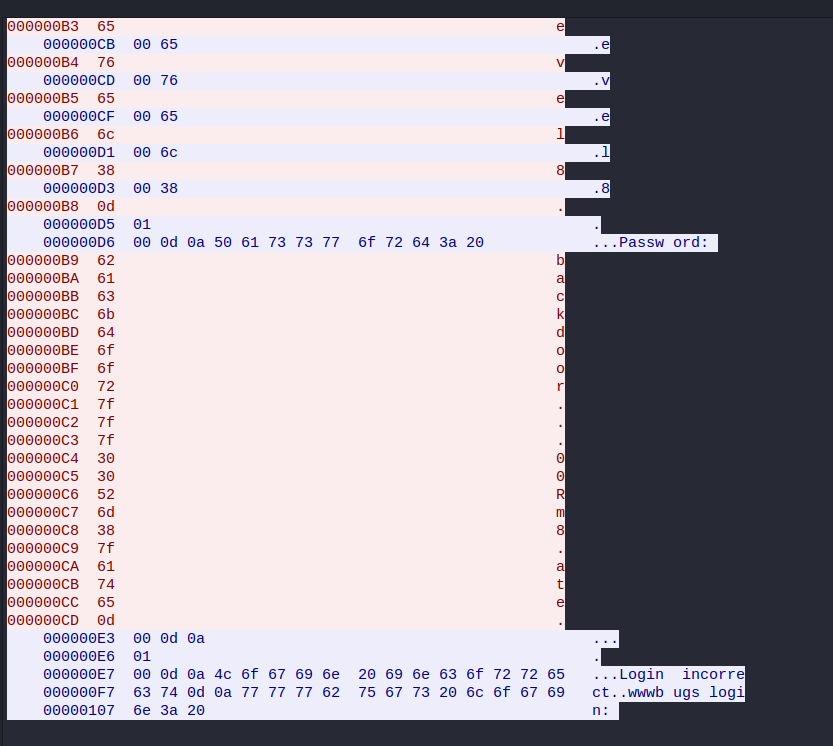
Exploit Exercises Stack 3 Walkthrough This stack exercise is going to build on the previous exercises and will look at changing the address of a jump command to change the flow of the program First let s look at the source code
Protostar is a virtual machine from Exploit Exercises that goes through basic memory corruption issues It is a step up from Nebula another virtual machine from Exploit Exercises that I have written about previously Quoting from the website Protostar introduces the following in a friendly way Network programming Byte order Handling sockets Code 75 commits Failed to load latest commit information nebula protostar gitignore LICENSE README md README md This Repo is a collection of my work related to the challenges at exploit exercicss Walkthroughs may or may not be found in the folders related to each challenge
Exploit Exercises Stack 3 Walkthrough
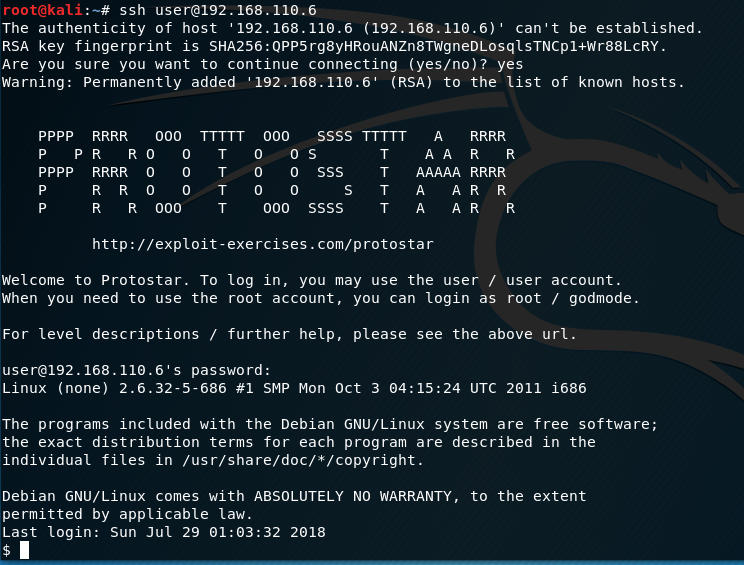
Exploit Exercises Stack 3 Walkthrough
https://miro.medium.com/max/744/1*VnLUbk3Cw-Ma0wfhwCcmAQ.png

Exploit exercises Desafio Hacker SECURITY MASTER
https://4.bp.blogspot.com/-RVtF8EJKkI8/T4LspSObrNI/AAAAAAAAAew/g9IVUrh3PKs/s1600/About-Exploit-Exercises.jpg

Exploit Exercises Protostar Stack0 Walkthrough YouTube
https://i.ytimg.com/vi/93i4hWM7IhE/maxresdefault.jpg
Exploit Exercises Protostar Stack Series In this series I will solve each of the seven levels of in from exploit exercises protostar You can find more info about the challenges here I will show you the source code and do my best to explain what is going on behind the scenes my thought process and how to solve and exploit each of the challenges n Use BOF to change the value of the function pointer fp make it point to the address of function win n Solution n
Follow 12 min read Apr 19 2018 Having previously tackled the last stack challenge in Protostar from Exploit Exercises In this walkthrough I will go over the stack exploitation portion of the wargame Spoiler Warning I would highly recommend you to go over the exercises yourself and come back to this article
More picture related to Exploit Exercises Stack 3 Walkthrough
Exploit Exercises Nebula v5 Walkthrough
https://ksdpmx.bitbucket.io/2020/09/13/exploit-exercises-nebula-v5-31/level08_wireshark.png

Exploit Exercises Protostar Stack 5 By Coturnix97 Medium
https://miro.medium.com/v2/resize:fit:1358/1*LBrcZgSxRJQWmJlOKX6Jcg.png

Exploit Exercises Fusion Level02
https://www.silentgrid.com/static/e144505e698d1203431a419a6236f0da/81a53/photo-1533912109441-e1eaa1dea549.jpg
Protostar is a series of exercises from Exploit Exercises In addition to three final levels it has four basic sections network programming format strings heap overflows and stack overflows This series of posts contains solutions and walkthroughs for the stack overflow levels Stack About Protostar introduces the following in a friendly way Network programming Byte order Handling sockets Stack overflows Format strings Heap overflows The above is introduced in a simple way starting with simple memory corruption and modification function redirection and finally executing custom shellcode
Exploiting Protostar Stack 0 3 April 3 2017 by Sahil Dhar In this article we will be reverse engineering and exploiting simple C programs from Protostar VM by exploit exercises We will be mainly focusing at how and why of stack overflows Exploit Education Phoenix Stack Three Solution July 9 2019 amlamarra Stack Three The description and source code can be found here https exploit education phoenix stack three This time we need to overwrite a function pointer that s being stored on the stack We need to get the program to call the complete level function

Exploit exercises Protostar Heap Walkthrough CSDN
https://img-blog.csdnimg.cn/20200809171905541.png?x-oss-process=image/watermark,type_ZmFuZ3poZW5naGVpdGk,shadow_10,text_aHR0cHM6Ly9ibG9nLmNzZG4ubmV0L0Nhc3VhbGw=,size_16,color_FFFFFF,t_70

The Periodic Table Of Dumbbell Exercises Is A Clickable Infograph Of 104 Dumb Bell Exercises
https://i.pinimg.com/originals/db/7f/df/db7fdf3114a41e117f036ace733ae363.jpg
Exploit Exercises Stack 3 Walkthrough - In this walkthrough I will go over the stack exploitation portion of the wargame Spoiler Warning I would highly recommend you to go over the exercises yourself and come back to this article