Binary Bomb Phase 3 Walkthrough Github Goals Solve a total of 6 phases to defuse the bomb Each phase has a password key that is solved through the hints found within the assembly code Become familiar with Linux VM and Linux command line Use and navigate through gdb debugger to examine memory and registers view assembly code and set breakpoints within the gdb debugger
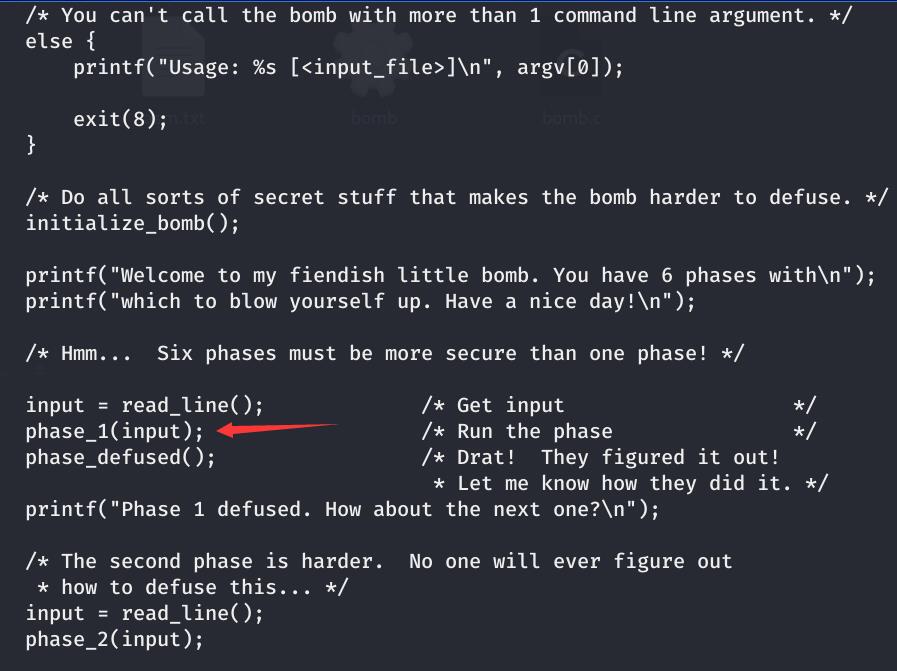
payload allShortcutsEnabled false fileTree items name Phase 4 path Phase 4 contentType file name Phase1 path Phase1 Secret Phase Phase 1 I fired up gdb added some breakpoints before and after the first input string required for the bomb Then I stepped through the disassembled instructions to find a function called phase 1 Note that between the beginning and end of phase 1 there is a call to the function strings not equal
Binary Bomb Phase 3 Walkthrough Github
Binary Bomb Phase 3 Walkthrough Github
https://media.cheggcdn.com/media/230/2309986a-80e9-46ca-b015-2dbc7405dbcb/phpXDSU75.png
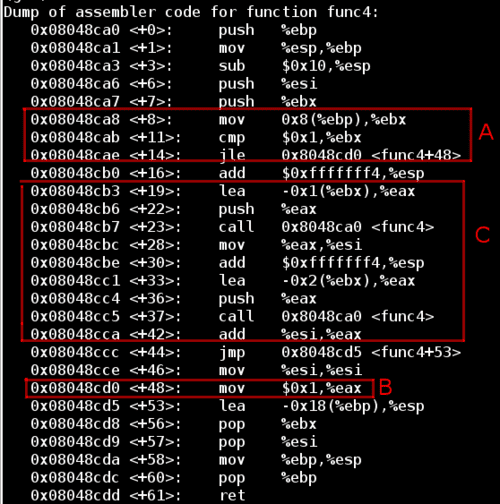
Defusing The Binary Bomb Vedran Budimcic
https://vedranb.com/static/d742c3aae64637203c12084bd47a33ef/7217d/44dd650fab5d0cf5d7666175549b911ee00d8f71819db03643d3156f869a7b2a.png
Solved Binary Bomb Phase 3 Can You Please Interpret What Chegg
https://media.cheggcdn.com/media/813/813de330-ce74-41dd-821a-1a348d7e3494/php6nYEtg
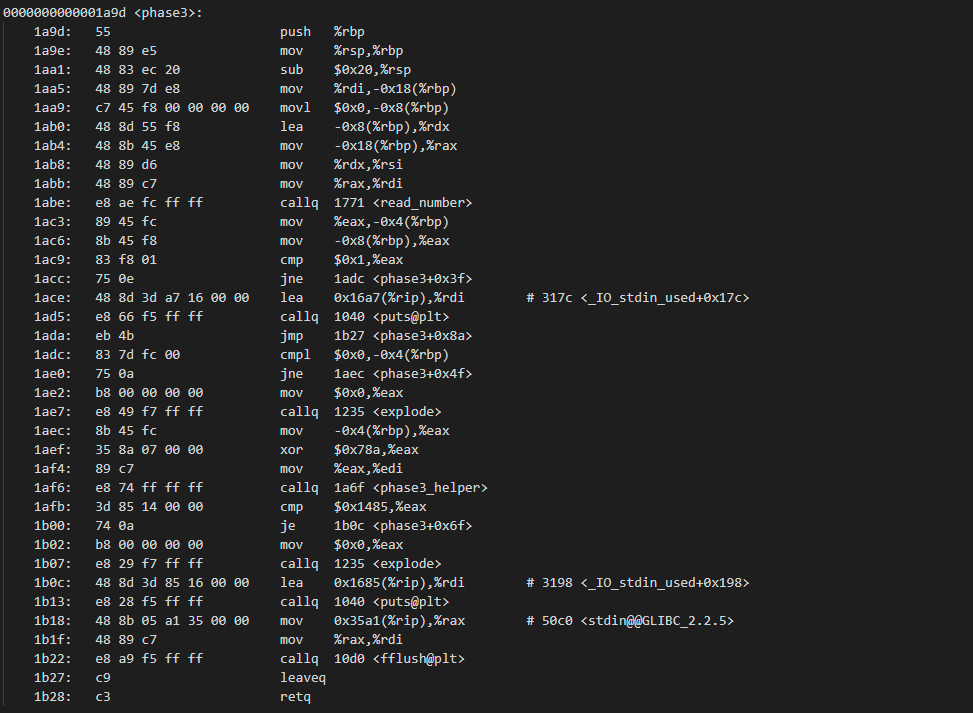
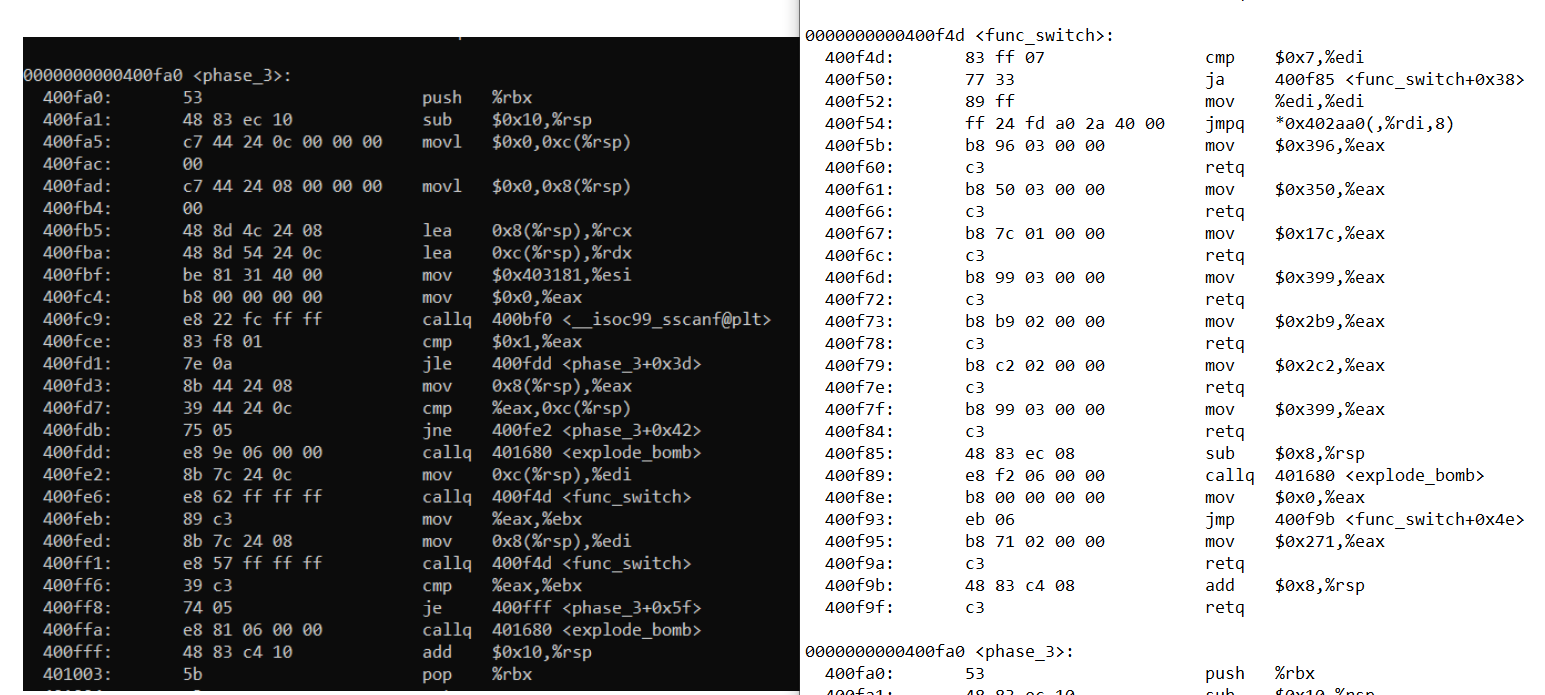
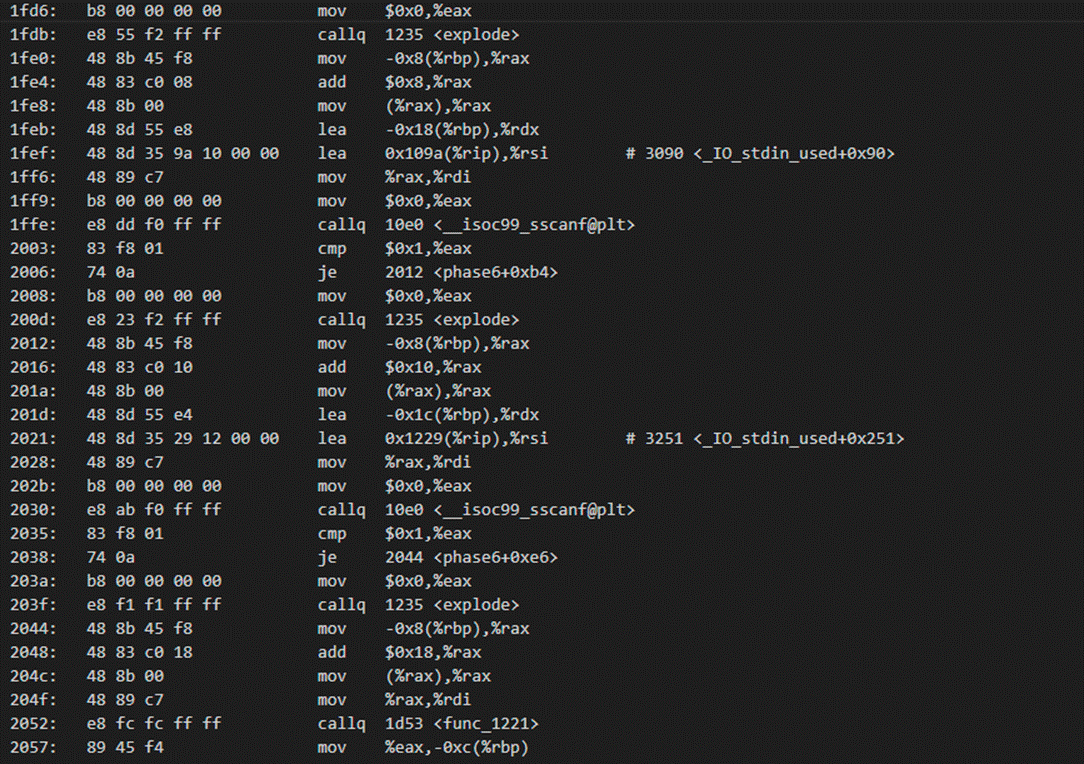
Binary Bomb Lab Phase 3 07 January 2015 A note to the reader For explanation on how to set up the lab environment see the Introduction section of the post If you re looking for a specific phase Here is Phase 1 Here is Phase 2 Here is Phase 4 Here is Phase 5 Here is Phase 6 By now you know the drill Off to our objdump file Woah Debugging so let s run the debugger and set a breakpoint on phase 3 before continue and enter a wrong answer for test let s analyze the code at first and see what it wants It starts same as last phase it calls sscanf again to check the format of the input if you examined the format parameter resides in 0x55555555730f you will see
Fork 1 Star 4 Code Issues 1 Pull requests Actions Projects Security Insights master README bomb lab solution In this repository I will take down my process of solving the bomb lab of CS APP Since there exists a bunch of different versions of this problem I ve already uploaded my version In this video I demonstrate how to solve the Bomblab Phase 3 for Computer Systems I assume that the student has already set up a VPN connection to a linux system running on an Intel x86 64
More picture related to Binary Bomb Phase 3 Walkthrough Github
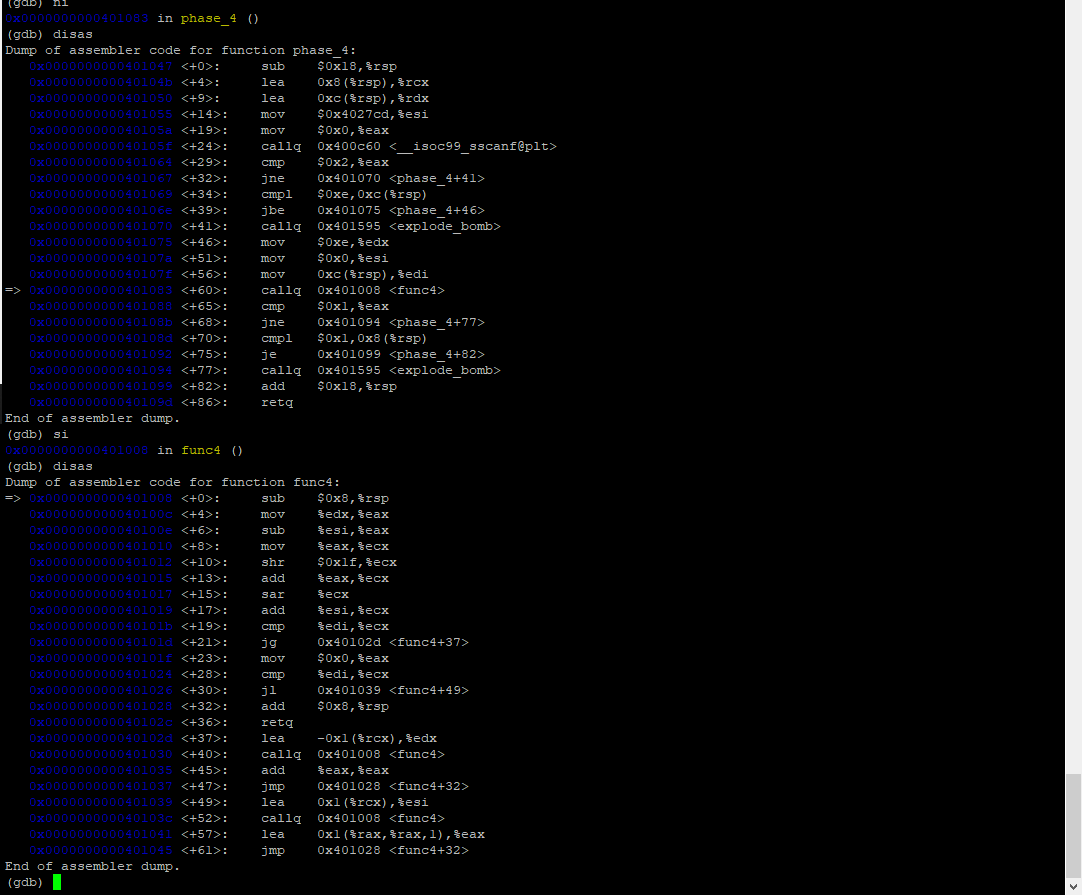
Solved This Is For The Binary Bomb Lab Phase 4 I Think The Chegg
https://media.cheggcdn.com/media/eeb/eeb01240-6c38-4691-852f-5c2d96a77600/phpj5Xny2.png
Binary Bomb Phase1 Pur3wh1tywhite
https://s1.ax1x.com/2020/03/20/82IcHs.jpg
Get Answer Binary Bomb Phase 6 Can You Please Interpret What This Assembly Transtutors
https://files.transtutors.com/book/qimg/88411d59-30d3-445d-9256-7f7f5c76dddb.png
OpenSecurityTraining Binary Bomb Walkthrough Phase 1Dr Gorgon s Binary Bomb Phase 3 Walkthroughhttps www youtube watch v 6QC j7mL2c4 t 2sSocial Media Phase 1 We can then set up a breakpoint upon entering phase 1 using b phase 1 and for the function explode bomb to avoid losing points Using layout asm we can see the assembly code as we step through the program Let s enter the string blah as our input to phase 1 When we hit phase 1 we can see the following code
Binary Bomb phase 3 stuck Ask Question Asked 8 years 11 months ago Modified 8 years 11 months ago Viewed 24k times 3 I am honestly very confused on this due to my bomb phase 3 not looking like any of my classmates or the example given to me by my professor Any help would be greatly appreciated payload allShortcutsEnabled false fileTree items name bomb answers txt path bomb answers txt contentType file name bomb tar path
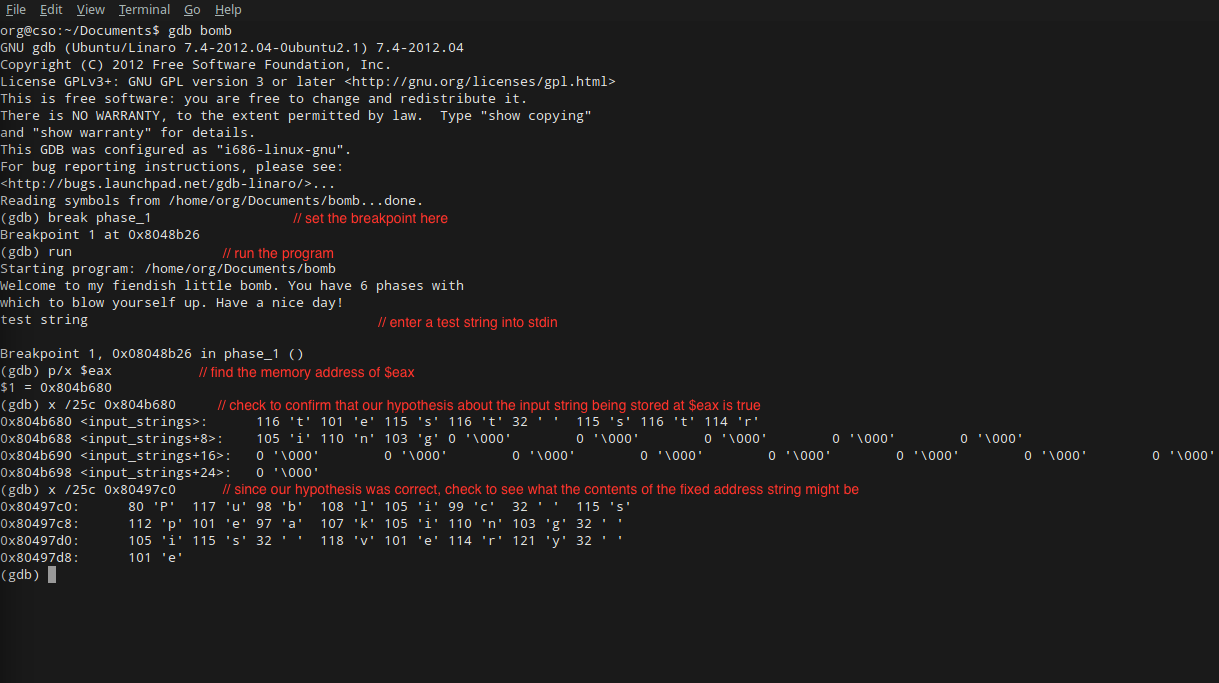
Binary Bomb Lab Phase 1
http://zpalexander.com/content/images/2016/05/phase-1-gdb.png
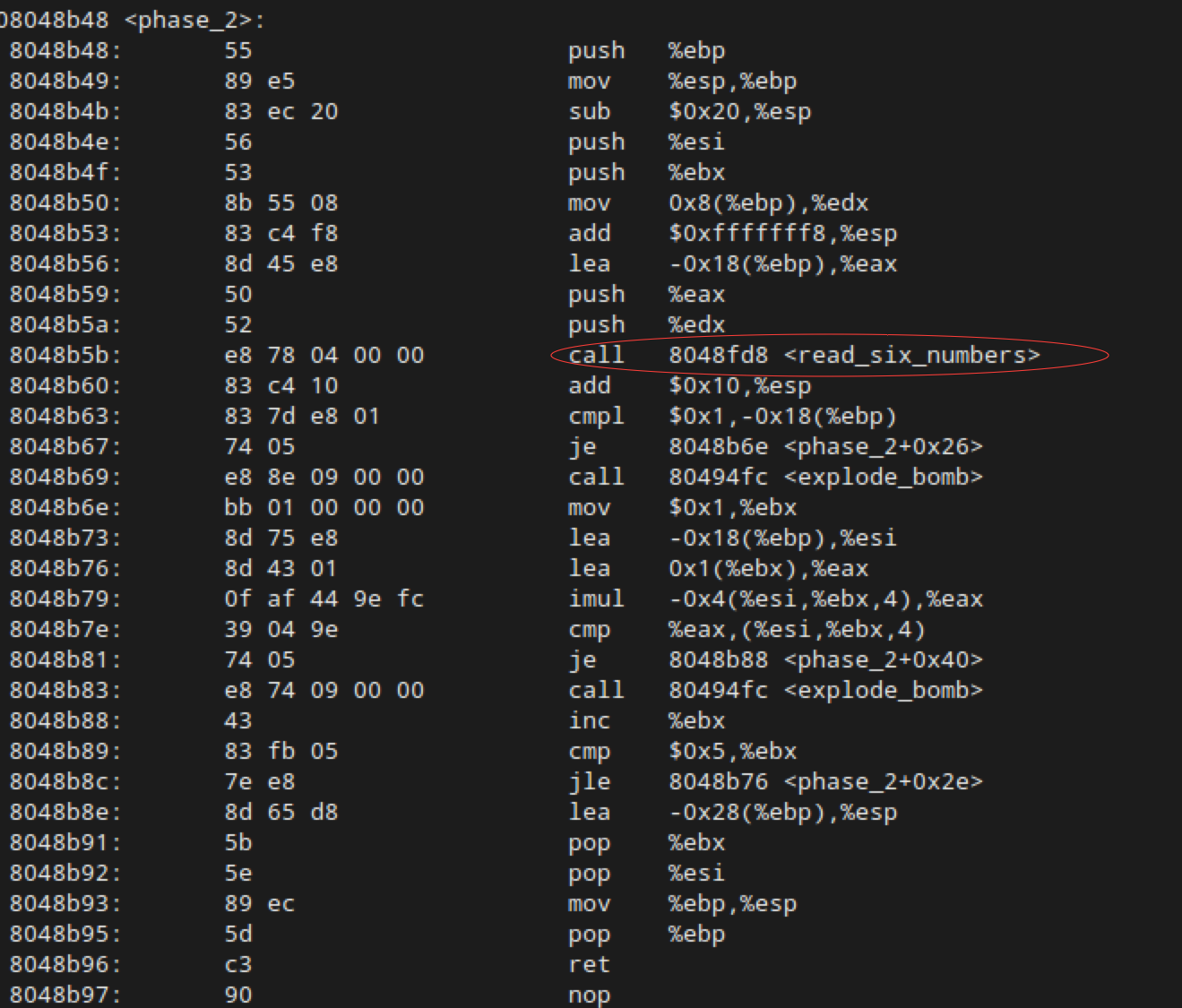
Binary Bomb Lab Phase 2
http://zpalexander.com/content/images/2016/05/phase-2-objdump1.png
Binary Bomb Phase 3 Walkthrough Github - Debugging so let s run the debugger and set a breakpoint on phase 3 before continue and enter a wrong answer for test let s analyze the code at first and see what it wants It starts same as last phase it calls sscanf again to check the format of the input if you examined the format parameter resides in 0x55555555730f you will see