Binary Bomb Lab Phase 3 Walkthrough Phase 1 jupyter Labs bomb439 gdb bomb Let s create our breakpoints to make sure nothing get s set to the gradebook gdb b explode bomb Breakpoint 1 at 0x4013ea gdb b phase 1 Breakpoint 2 at 0x400e2d Let s run it and test things out gdb run Starting program home jovyan Labs bomb439 bomb Welcome to my fiendish little bomb
Phase 3 Phase 4 Phase 5 Phase 6 Secret Phase Phase 1 I fired up gdb added some breakpoints before and after the first input string required for the bomb Then I stepped through the disassembled instructions to find a function called phase 1 Note that between the beginning and end of phase 1 there is a call to the function strings not equal 211 Share 38K views 3 years ago Computer Systems In this video I demonstrate how to solve the Bomblab Phase 3 for Computer Systems I assume that the student has already set up a VPN
Binary Bomb Lab Phase 3 Walkthrough
Binary Bomb Lab Phase 3 Walkthrough
https://media.cheggcdn.com/media/eeb/eeb01240-6c38-4691-852f-5c2d96a77600/phpj5Xny2.png
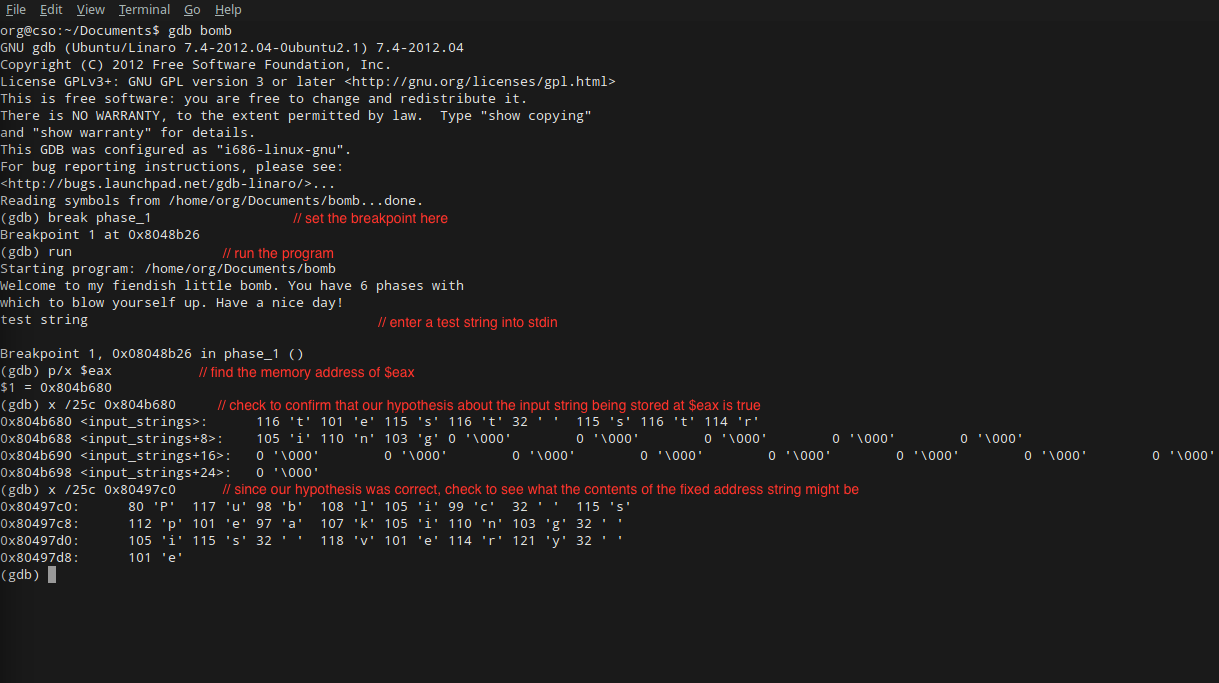
Binary Bomb Lab Phase 1
http://zpalexander.com/content/images/2016/05/phase-1-gdb.png
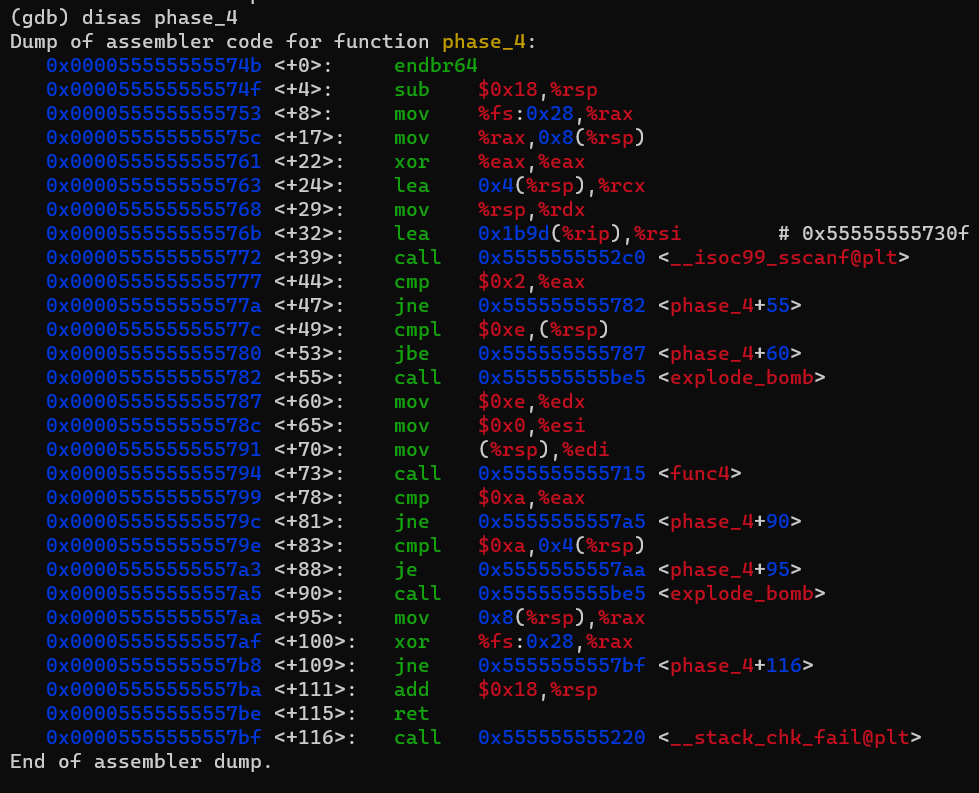
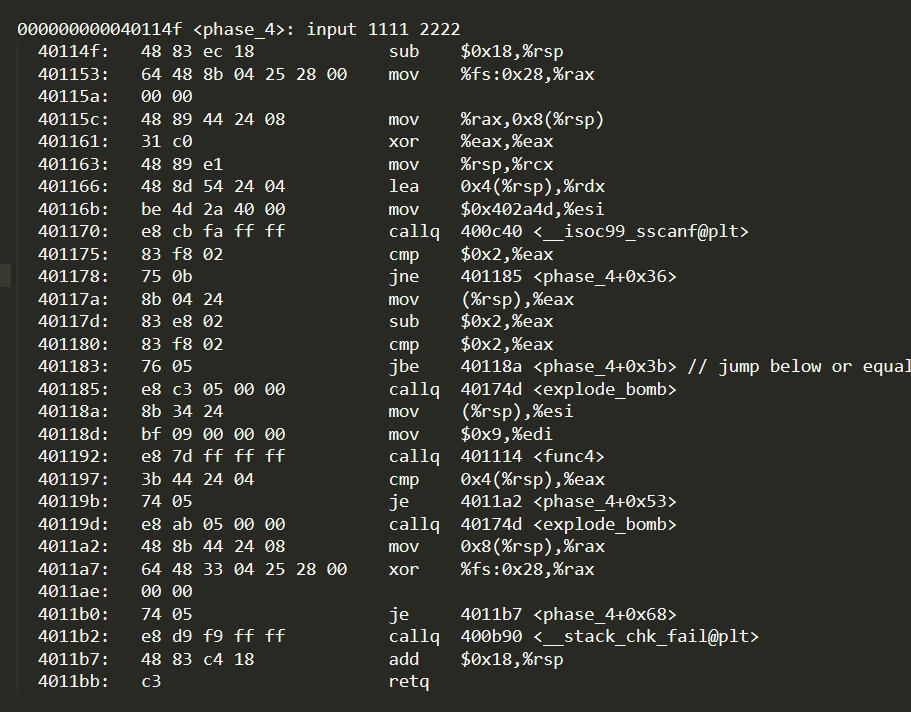
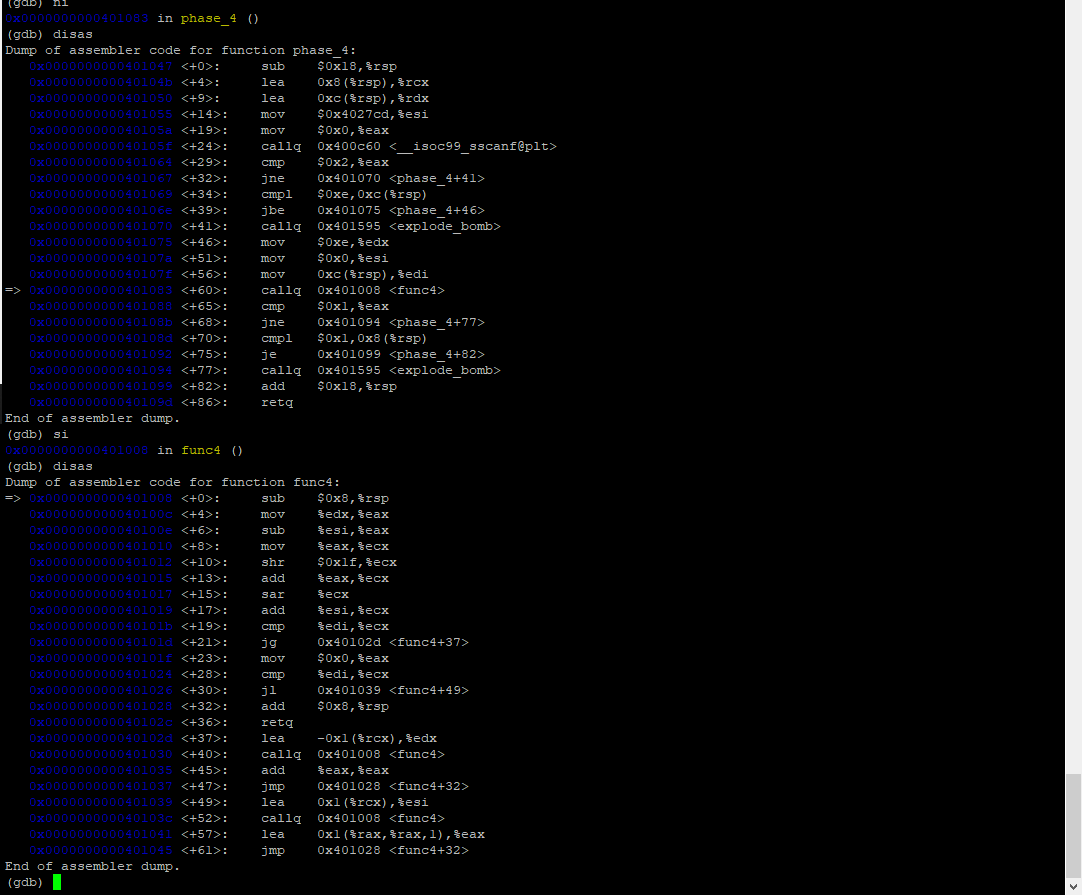
Binary Bomb Lab Phase 4 0xEFE4
https://omarshehata11.github.io/assets/images/reverseEngineerinig/phase4/1.png
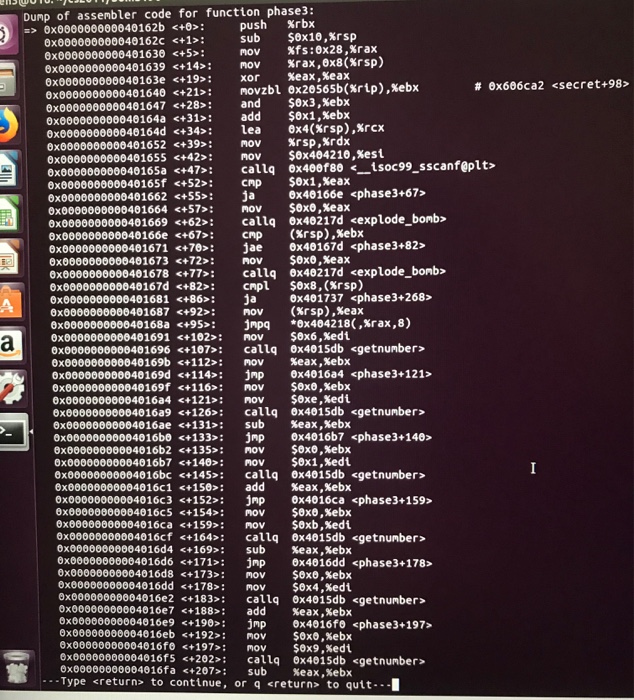
Debugging so let s run the debugger and set a breakpoint on phase 3 before continue and enter a wrong answer for test let s analyze the code at first and see what it wants It starts same as last phase it calls sscanf again to check the format of the input if you examined the format parameter resides in 0x55555555730f you will see 1 Yes this is homework and no I m not asking you to do my homework I need help with phase 3 of this binary bomb I didn t have any trouble with phases 1 and 2 but phase 3 is just too much for me I understand that there should be 3 inputs
Gorgon s Binary Bomb Phase 3 Walkthroughhttps www youtube watch v 6QC j7mL2c4 t 2sSocial Media Goals Solve a total of 6 phases to defuse the bomb Each phase has a password key that is solved through the hints found within the assembly code Become familiar with Linux VM and Linux command line Use and navigate through gdb debugger to examine memory and registers view assembly code and set breakpoints within the gdb debugger
More picture related to Binary Bomb Lab Phase 3 Walkthrough
I Am Stuck On Doing This Phase Of The Binary Bomb Lab Chegg
https://media.cheggcdn.com/media/ce5/ce5e86fc-cd07-405b-813f-2ed25bbd9f4c/phpfU3mLY
Solved BInary Bomb Lab Phase 5 Help I Don t Know How To Get Chegg
https://media.cheggcdn.com/media/ef1/ef13920b-fbb4-4c21-bc99-2b3931e733bb/phpzHxDIc
Solved This Is The Bomb Lab Phase3 What Is The Right Input Chegg
https://media.cheggcdn.com/media/6d4/6d4cda85-6db8-4c5a-8e36-696664c8b975/image
This post walks through CMU s bomb lab which involves defusing a bomb by finding the correct inputs to successive phases in a binary executable using GDB Post Outline Intro GDB Phase 1 Phase 2 Phase 3 Resources Intro This post walks through the first 3 phases of the lab I used a linux machine running x86 64 payload allShortcutsEnabled false fileTree items name Phase 4 path Phase 4 contentType file name Phase1 path Phase1
Load the binary analyze it seek to sym phase 3 then print it Despite first impressions this function isn t very complicated and with Graph mode we can easily make sense of it Enter Graph mode mode with the command capital VV then move around with the arrow keys or hjkl la vim Exit by pressing qq CS3330 Lab 1 Bomb Lab CS 3330 Spring 2018 HWs Labs This is the website for a prior semester s offering of CS 3330 A Mad Programmer got really mad and planted a slew of binary bombs on our class machines A binary bomb is a program that consists of a sequence of phases Each phase expects you to type a particular string on
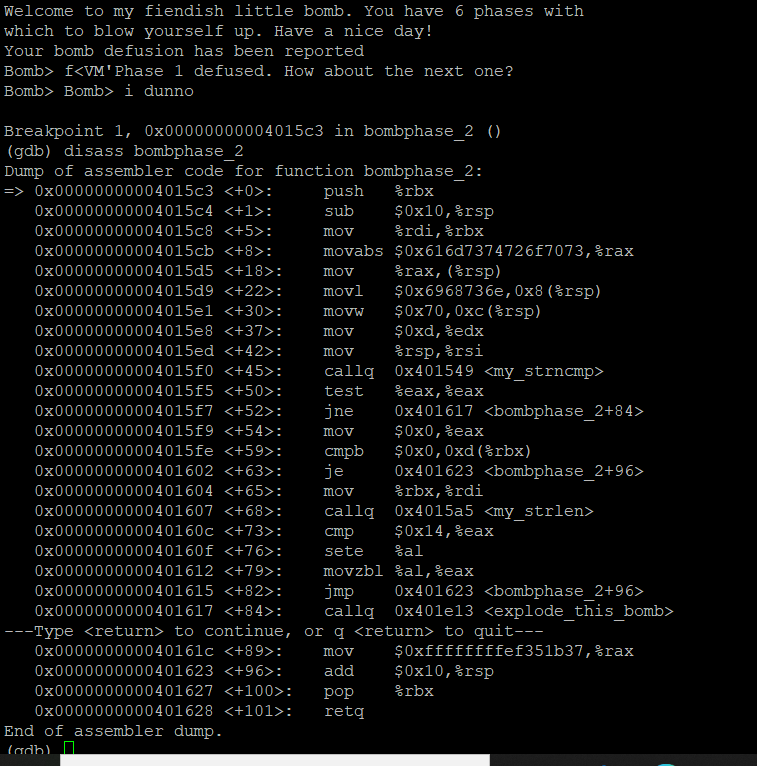
Get Answer I Am Stuck At Binary Bomb Lab Phase 2 Task These Are The Transtutors
https://files.transtutors.com/book/qimg/9c8088ce-1651-480d-a7b1-0b35361aed5e.png
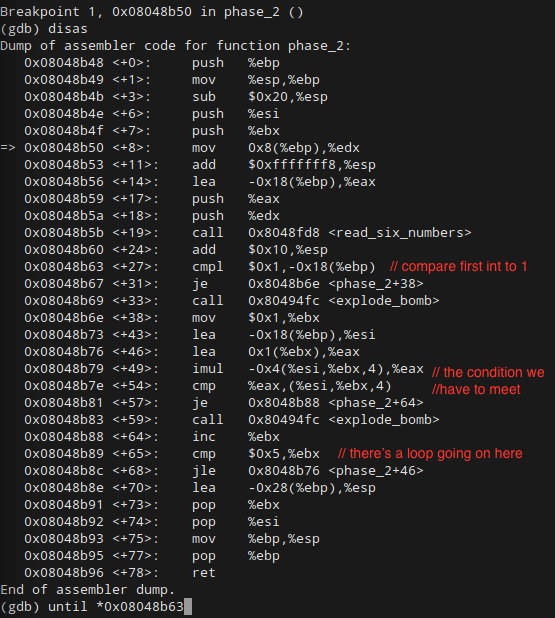
Binary Bomb Lab Phase 2
http://zpalexander.com/content/images/2016/05/phase-2-disas.png
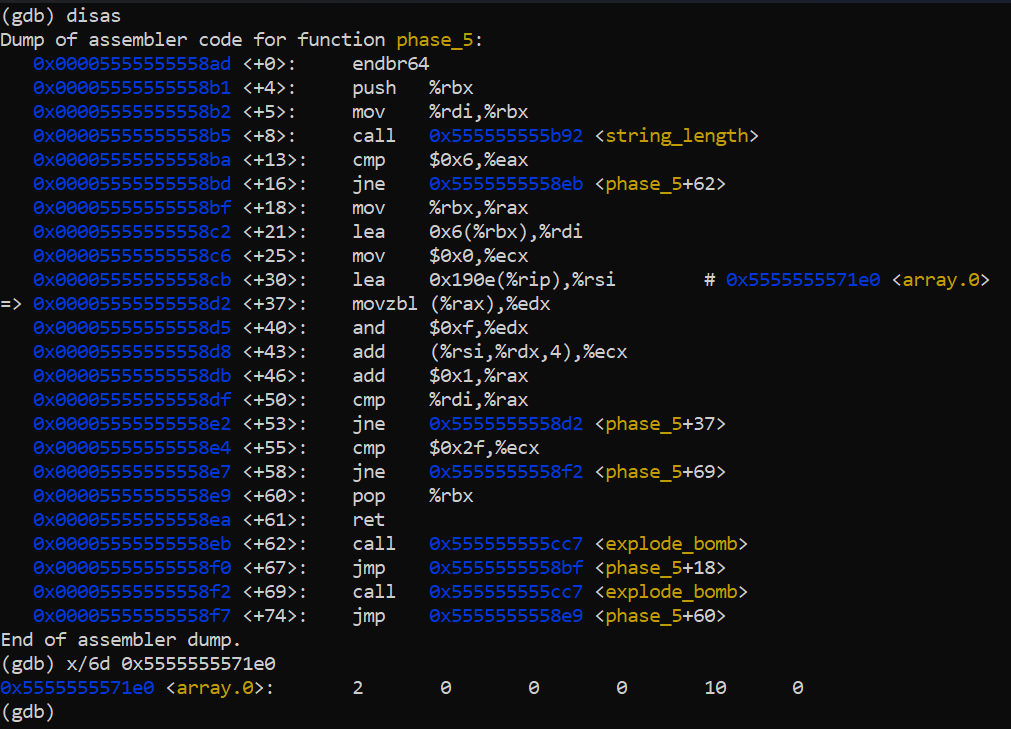
Binary Bomb Lab Phase 3 Walkthrough - Let s go with 47 Load the binary with r2 and answers txt in Debug mode use dcu sym secret phase to break at our function and step through it After calling sym fun7 and entering the function look at the values at rdi arg1 and the value of rsi arg2 Arg1 is set to 36 the value of obj n1