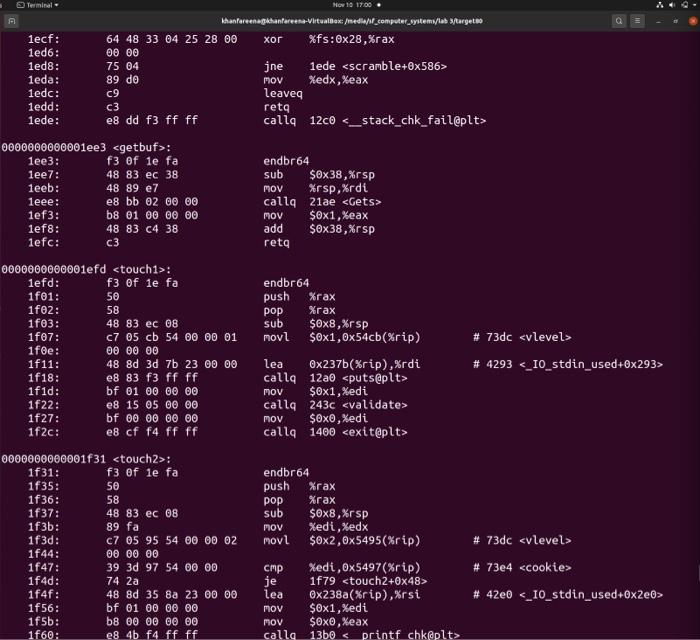
Attack Lab Phase 3 Walkthrough After I got stuck at phase 3 I don t know why I looked up a solution which is slightly different than my approach https programmerah csapp experiment 3 attack lab 21351 see section phase 3 I have written 48 c7 c7 b0 dc 61 55 this row starts at address 0x5561dc78
Attack Lab A brief walkthrough of the buffer overflow attack known as Attack Lab or Buffer Bomb in Computer Systems course There are 5 phases of the lab and your mission is to come up with a exploit strings that will enable you take control of the executable file and do as you wish Attacklab Phase 3 YouTube 0 00 4 29 Attacklab Phase 3 Arsalan Chaudhry 117 subscribers Subscribe Subscribed 38K views 6 years ago Made this really quick but it should give an idea of how
Attack Lab Phase 3 Walkthrough

Attack Lab Phase 3 Walkthrough
https://i.ytimg.com/vi/Z0B7ebyRHUA/maxresdefault.jpg
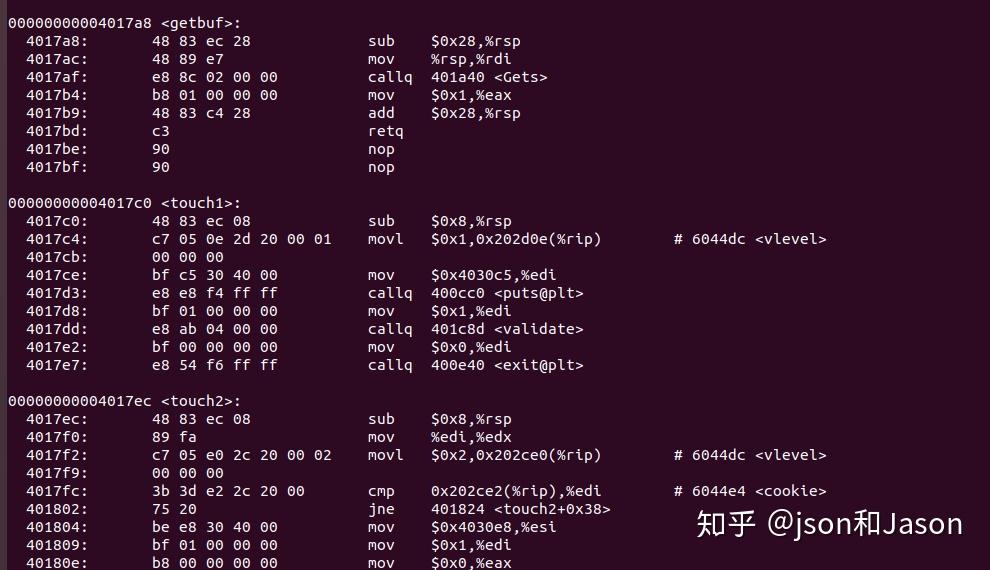
Attack Lab
https://pic3.zhimg.com/v2-e337c64dfe03caa40fd9f4cb6006b05a_r.jpg
Attack Lab Phase 1 Assembly What Am I Doing Wrong Chegg
https://media.cheggcdn.com/study/e19/e19ec632-d64f-480a-8b55-f54b1ad74e8a/image
You called touch3 19195f9f nValid solution for level 3 with target ctarget nPASS Sent exploit string to server to be validated nNICE JOB pre span class pl ent Cookie span span class pl c1 0x19195f9f span n span class pl s1 Type span span class pl ent string span span class pl ent Touch3 span span c Attack Lab Phase 3 Course Work Computer Organization and Architecture Attack Lab Less than 1 minute About 277 words Run gdb ctarget tui gdb break getbuf Breakpoint 1 at 0x401b28 file buf c line 12
Figure 1 Summary of attack lab phases 4 1 Level 1 For Phase 1 you will not inject new code Instead your exploit string will redirect the program to execute an existing procedure Function getbuf is called within CTARGET by a function test having the following C code 1 void test 2 3 int val 4 val getbuf 5 printf No exploit Getbuf And your students will have to get new targets and start over 2 Starting the Attack Lab make start runs attacklab pl the main daemon that starts and nannies the other programs in the service checking their status every few seconds and restarting them if necessary 3 Stopping the Attack Lab make stop kills all of the running servers
More picture related to Attack Lab Phase 3 Walkthrough

Attack Lab Phase 3 YouTube
https://i.ytimg.com/vi/KEwSIy_hcVM/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH6CYAC0AWKAgwIABABGGQgZChkMA8=&rs=AOn4CLCKgPYL17s687WGxrYmjwzMP87ooA

Attack Lab Cuzz s Blog
http://img.cuzz.site/20220207181100.jpg

Attack Lab Phase 2 YouTube
https://i.ytimg.com/vi/769S3so1hj4/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH-CYAC0AWKAgwIABABGDEgUyh_MA8=&rs=AOn4CLBTP3udDA9SwuBbP6ER2Frx9jUV9A
payload allShortcutsEnabled false fileTree items name Attack Lab Notes path Attack Lab Notes contentType file name Attack Lab Phase This post walks through CMU s Attack lab which involves exploiting the stack space of vulnerable binaries Post Outline Level 1 Resources We go over Level 1 in this post Level 1 From the assignment handout we are told that there is a function test that calls getbuf We want getbuf to call touch1 in this first phase
Attack Lab Overview Phases 4 5 Overview Utilize return oriented programming to execute arbitrary code Useful when stack is non executable or randomized Find gadgets string together to form injected code Key Advice Use mixture of pop mov instructions constants to perform specific task Attack Lab Goal 5 attacks to 2 programs to learn How to write secure programs Safety features provided by compiler OS Linux x86 64 stack and parameter passing x86 64 instruction coding Experience with gdb and objdump Rules Complete the project on the VM Don t use brute force server overload will be detected

Keeping Our Edge The Attack Lab LaptrinhX News
https://www.ledger.fr/wp-content/uploads/2019/03/Attack-Lab_Twitter-1000x563.png

Attack Lab Phase 4 YouTube
https://i.ytimg.com/vi/NpuXTKuLJe4/maxresdefault.jpg?sqp=-oaymwEmCIAKENAF8quKqQMa8AEB-AH-CYAC0AWKAgwIABABGGUgSShTMA8=&rs=AOn4CLClhvG5CTRMwvAebdB2Us2bD2Iv8g
Attack Lab Phase 3 Walkthrough - This experiment can refer to section 3 10 3 and 3 10 4 of CS app3e If RET command is used to attack the address should be one of the following 0 The address of the function touch1 touch2 or touch3 is used to inject code When constructing gadgets from rtarget file the address should be in start Farm and end Between farms